Certified ethical hackers (CEH) entering the cybersecurity industry, you know you have to make a choice.
You can take the blue pill - and it's time to face the music. Your role would be to guard all systems against incoming threats and attacks.
Or, you can take the red pill - to find out how deep the rabbit hole of potential vulnerabilities goes.
CEHs are set to become crucial to a more secure digital space in the next decade or so.
In the past year, we've seen how cyber warfare has become a lethal weapon in the war between Russia and Ukraine.
Or how hybrid work in the post-pandemic normal has heightened the risk of cyberattacks.
Some companies are just starting to realize that:
"If you spend more on coffee than on IT security, you'll be hacked."
Richard A. Clarke, American national security expert, novelist, and former government official
Certified professionals now have plenty of opportunities on their hands: to join these dynamic times on the offensive cyber team of companies.
But how do you go about transforming your professional experience into a curated resume to catch the recruiters' eye?
Here's where our guide comes in. We'd help you to audit and assess your resume for potential weaknesses, flaws, and vulnerabilities.
Use our experts' advice on how to make the most out of your certificates, education, and experience - even if you don't have much.
Because we know that you can land that dream job: all you need to do is follow a proactive, targeted approach.
Sort of like the one you have to assess systems and prevent cyberattacks.
What you’ll learn here
- How to curate your cybersecurity experience to include as many of your technical skills and projects as possible?
- Five writing tips to kick off your resume summary + BONUS one.
- How junior professionals, looking for CEH opportunities, could make their experience stand out?
- Why is including your personal projects and virtual labs such a good idea for certified ethical hackers?
- 50+ skills you need to add to your CEH resume.
Looking for related resumes?
- Cyber Security Analyst
- IT Security Manager
- Network Security Engineer
- Security Analyst
- Security Director
- System Analyst
- IT Audit Manager
- Network Engineer
- Computer Engineer
- Service Desk Manager
- Technical Support Manager
- Desktop Support
- Help Desk
How to write a certified ethical hacker resume
Certified ethical hackers are sort of like the knights of cybersecurity justice. On a day-to-day basis, they're on the front line:
- assessing systems for potential bug bounties, especially security flaws;
- unmasking weaknesses to demonstrate possible threats to online security;
- managing the risk of possible cyberattacks and compromises;
- following a security code of ethics.
To prepare your resume for the role of your dreams, first, consider your expertise in these three elements.
- Computer networks
Think about the network security audits, penetration tests, and cryptography practices you've installed.
What was their effect on the overall organization's security?
- Operating (and physical) systems
Here is where big-picture thinking comes in, with a two-system focus.
You've probably had to do some admin work in Linux (CLI) and Windows. Note on your resume the ways you've discovered to strengthen both operating systems.
Physical security is all about keeping employees informed and following best security practices. Because joining a public Wi-Fi or leaving your company laptop unattended could lead to more serious precautions.
- Internet and apps
Do you have experience in simulating attacks to test the "human error" side of the organization?
Web security and management are definitely skills that you'd like to highlight on your resume. They show that you can consider all system flaws.
Now that you've sort of outlined your strengths and expertise, it's time to think about:
What recruiters want to see on your certified ethical hacker resume
- What was the outcome of the audits and system tests you performed? How did your recommendations strengthen organizations’ cybersecurity?
- What sort of experience do you have working in different environments in regard to tools and timeframes?
- If you don’t have much professional experience, do you have personal projects that could be relevant to the job you’re applying for?
- Do you have all the relevant certifications/education to perform the job?
- Are you apt at preparing reports and communicating across different organizational levels?
After drafting your resume profile, it's time to get to work.
Find three-to-five roles you'd like to apply for. Within the requirements, search for must-have certifications and skills. Demonstrate those within your resume via experience and outcomes.
Alternatively, you could decide to select find three companies you'd like to work for. Forward them your resume and cover letter, both targeted for a potential role.
You never know where opportunities could come from.
Before we continue with the rest of this guide, here are:
Five key certified ethical hacker resume sections to focus on
- Professional Experience: In Different Environments
- Relevant Cybersecurity Certificates
- Personal Projects and Open Source Contributions
- Higher Education
- Technical and Personal Skills
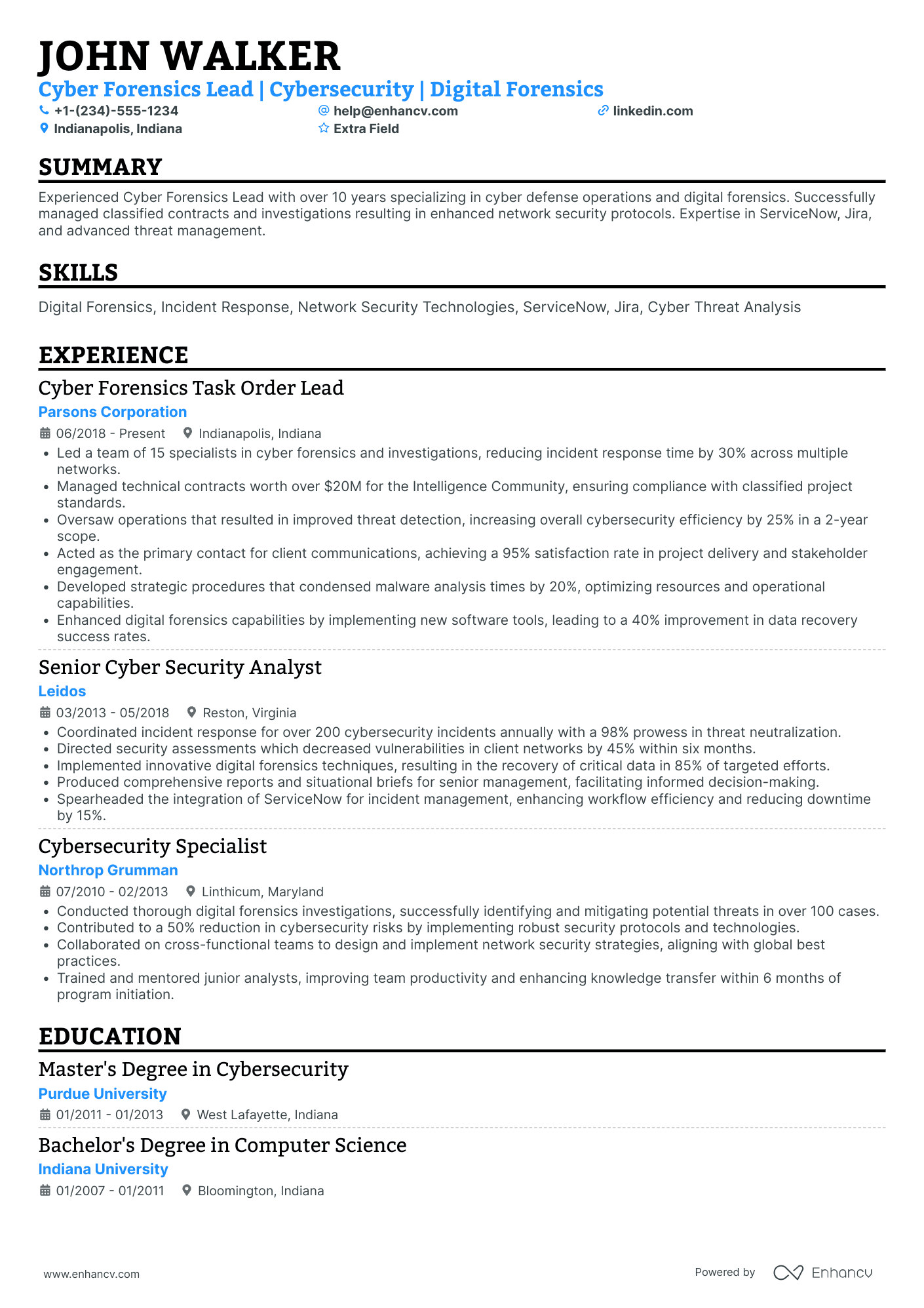
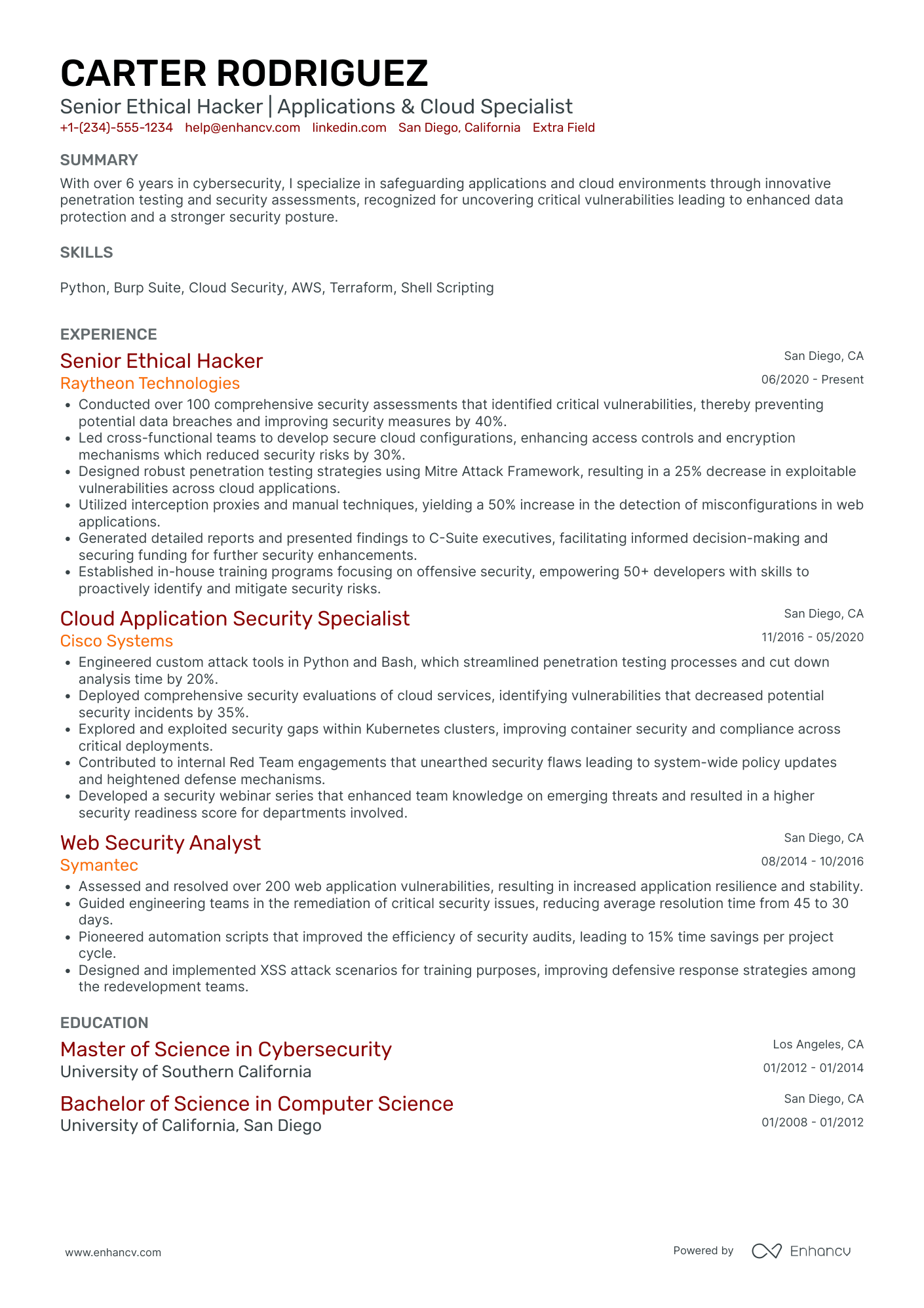
Certified ethical hacker resume header
Let's start with the basics of every resume header.
Scanning over this section, recruiters or the Applicant Tracker Systems (ATS) have to quickly find your contact details: relevant email address and telephone number.
Next comes the headline. Within this section, you can include keywords from the job advert, your certification, and/or most recent experience. Consider what's important to the job you're applying for.
Last, but not least, your potential employees and/or recruiters need to be able to preview your previous work. So, a GitHub link to your portfolio would work magic.
We'll get into more details on what you can include in the projects section of your resume, but for now, let's look at:
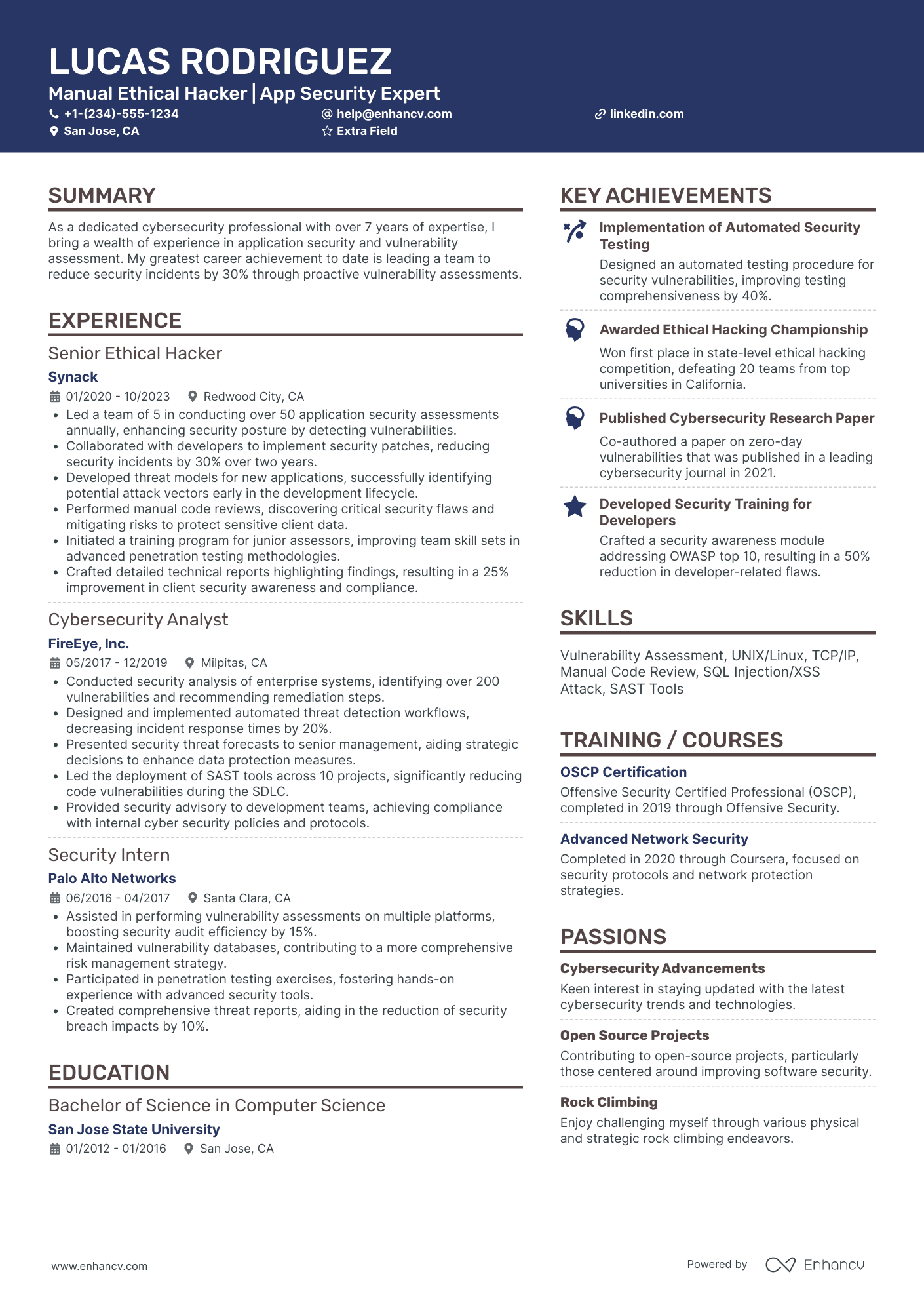
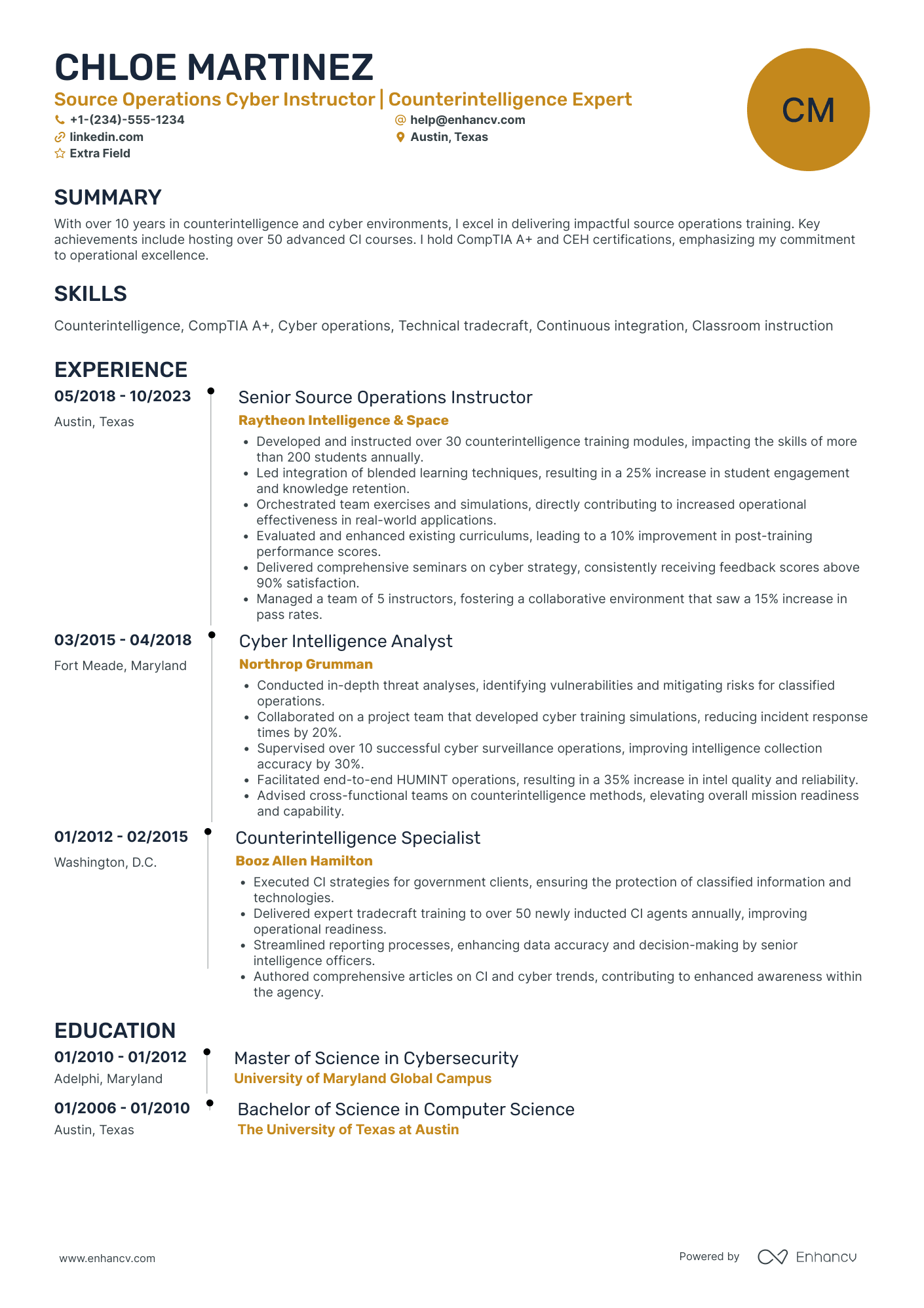
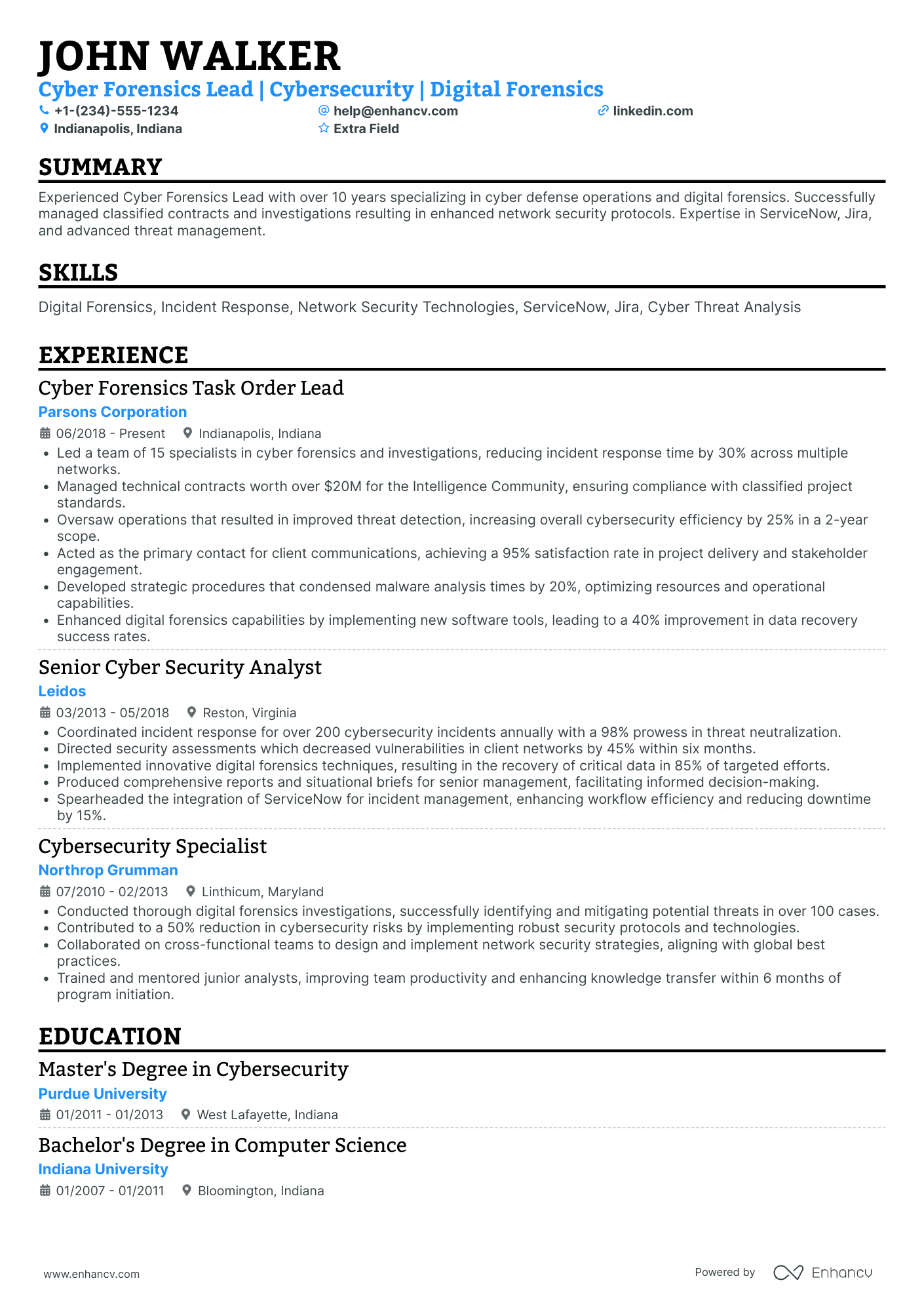
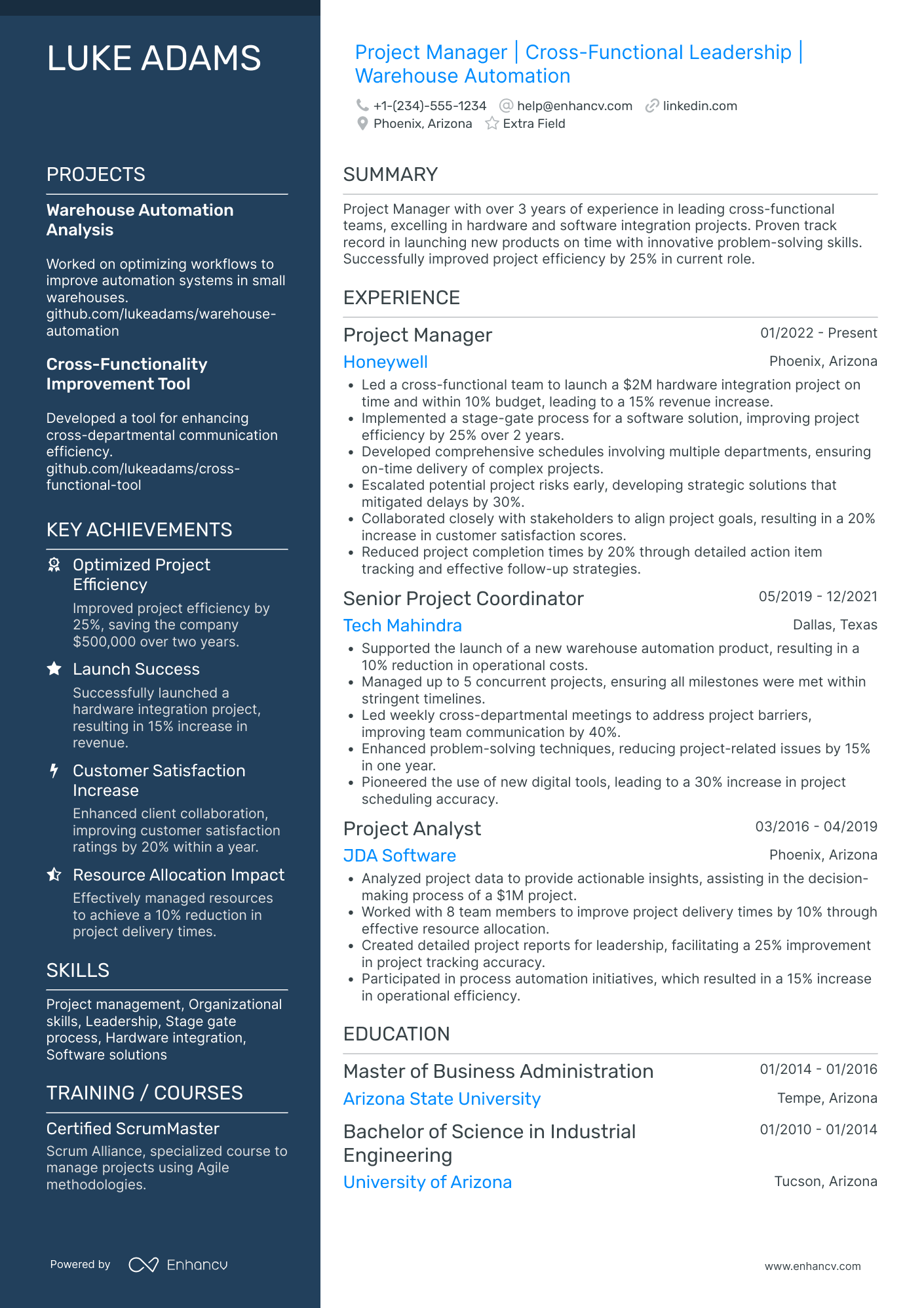
2 certified ethical hacker resume header examples
The above example doesn’t meet standard header criteria as the:
- Headline or title is generic
- Email is unprofessional
- Personal Facebook (or Meta) profile isn’t a relevant link - perhaps - for recruiters
The above example has all the correct contact details and professional links.
The headline serves three functions: pinpointing the certification; soft skill and mindset; and actual outcomes of the role.
Certified ethical hacker resume summary go-to strategy
The resume summary is the section everyone tends to struggle with, and that's understandable.
Because how can anyone narrow their experience down to three-to-five sentences that ultimately sell you as the perfect candidate?
If you're a certified ethical hacker, facing the same dilemma, here are five elements you can highlight within your resume summary.
1. Certification - all recruiters follow a checklist when assessing your resume. Obviously, your cybersecurity certificates are at the top of their list. Hence, make sure you've included yours.
2. Years of experience in the industry and within different environments. This shows adaptability, yearning for knowledge, and consistency.
3. Biggest personal or professional achievement(-s) of your career. This can be something massive - like decreasing the number of cyberattacks on organizational systems by 87% by patching vulnerabilities. Or something you've discovered within your virtual lab.
4. Soft skills. Consider all of those small bits and pieces that make you the professional you are today. Those could include work ethics, communication style, problem-solving, etc. Don't forget to show how your soft skills have impacted your work.
5. In spite of your role being highly technical, there's a personal element that would set you apart from everyone else. Are you apt at communicating with professionals from different levels of the organization? This is a winning skill to always highlight in your resume summary.
BONUS - yes, we've prepared one more tip to make your CEH resume really stand out.
Pro tip
Tailor your summary to the role you're applying for by aligning the organizational requirements with your own skills, expertise, and values.
This way, everyone stays on the same page regarding what matters the most and the necessary qualities, through the recruitment process.
Optimize your resume summary and objective for ATS
Drop your resume here or choose a file.
PDF & DOCX only. Max 2MB file size.
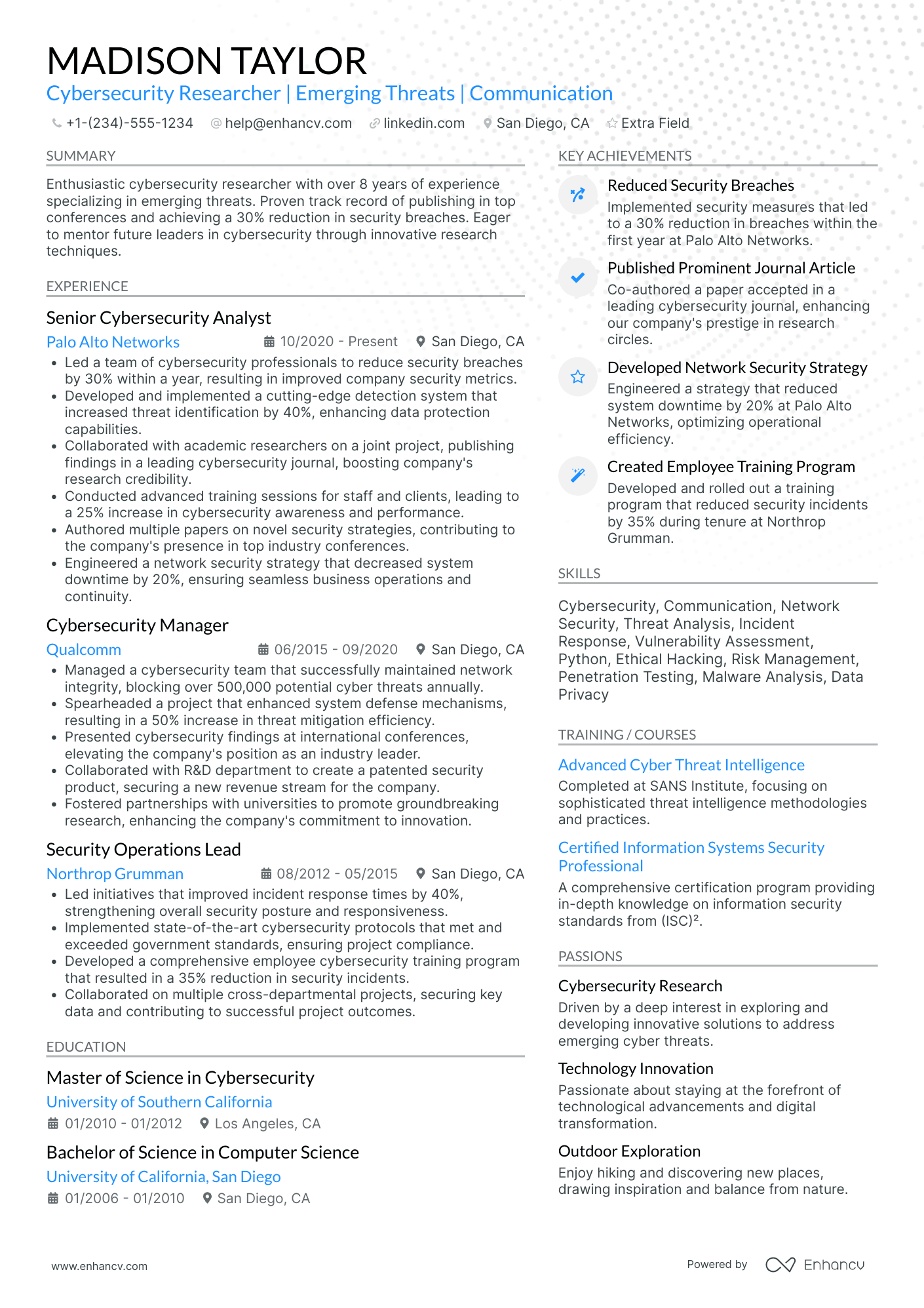
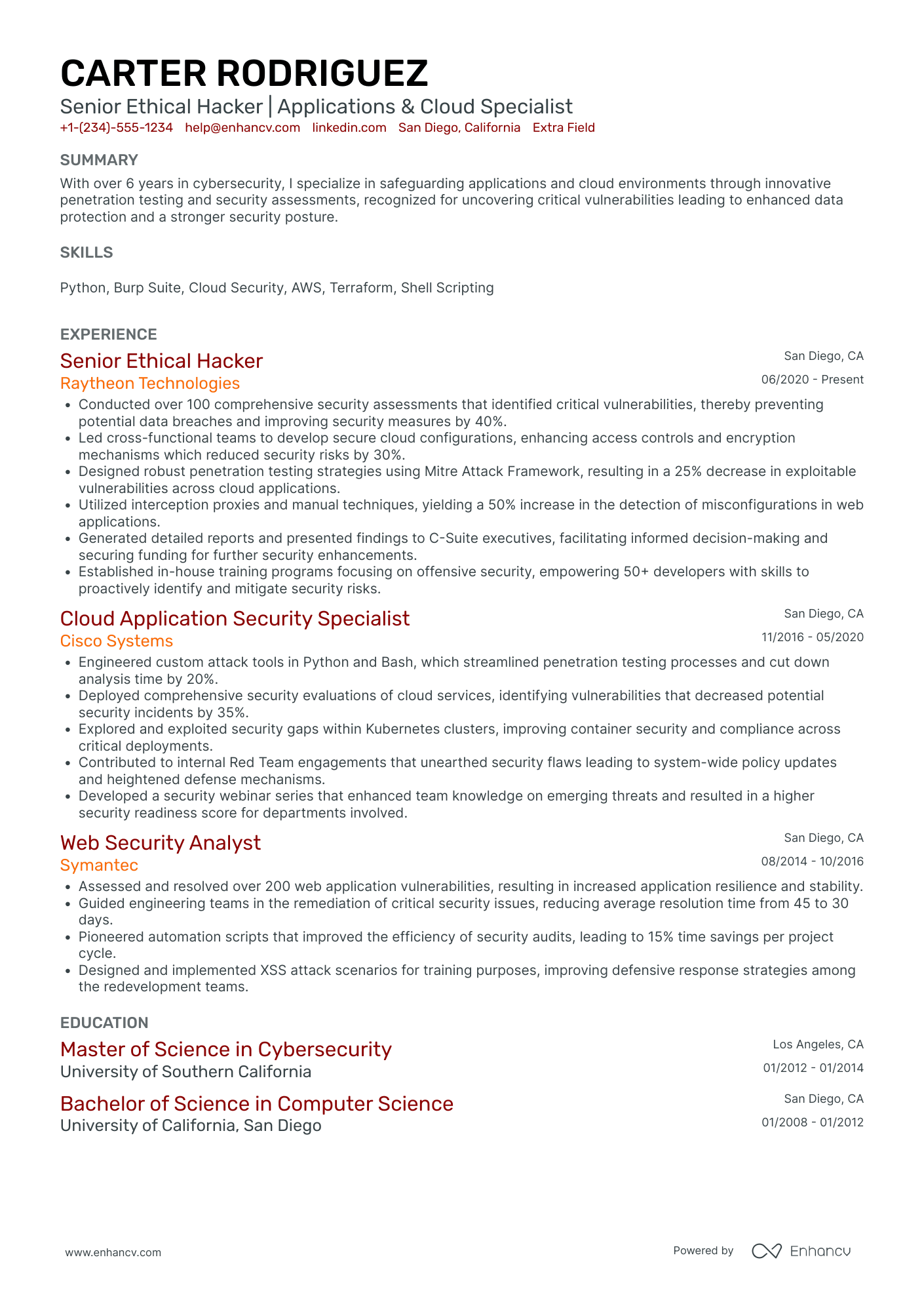
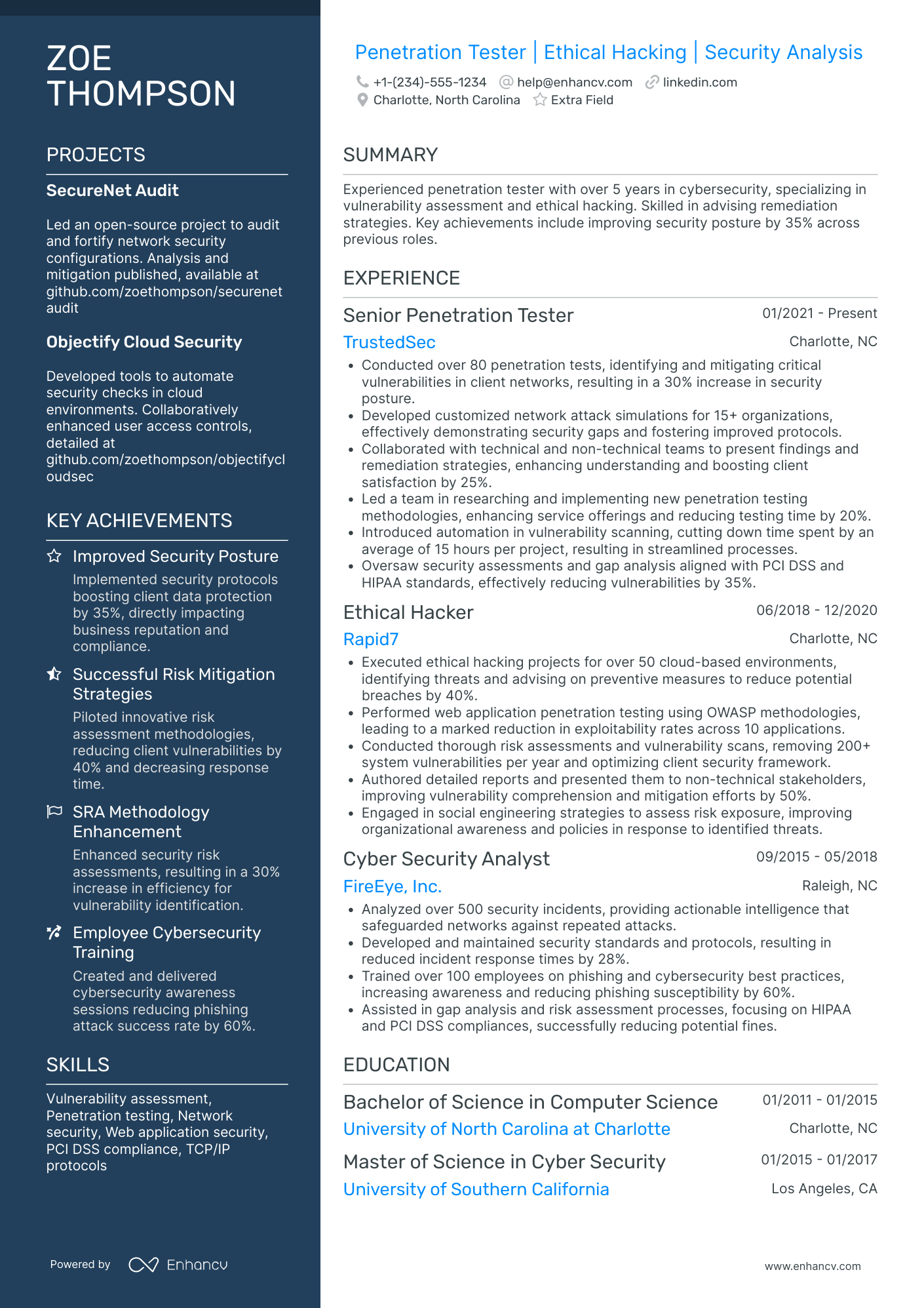
2 certified ethical hacker resume summary examples
The word ‘hacker’ most certainly has negative connotations within the industry. Within the first sentence, you’d immediately question the ethics and credibility of this professional.
The next two sentences go on to list keywords from the job requirements without any specific context.
While it’s important to show character in your resume summary, dedicating space to noting your hobbies could be better suited for other resume sections (e.g. quotes, my hobbies, my time).
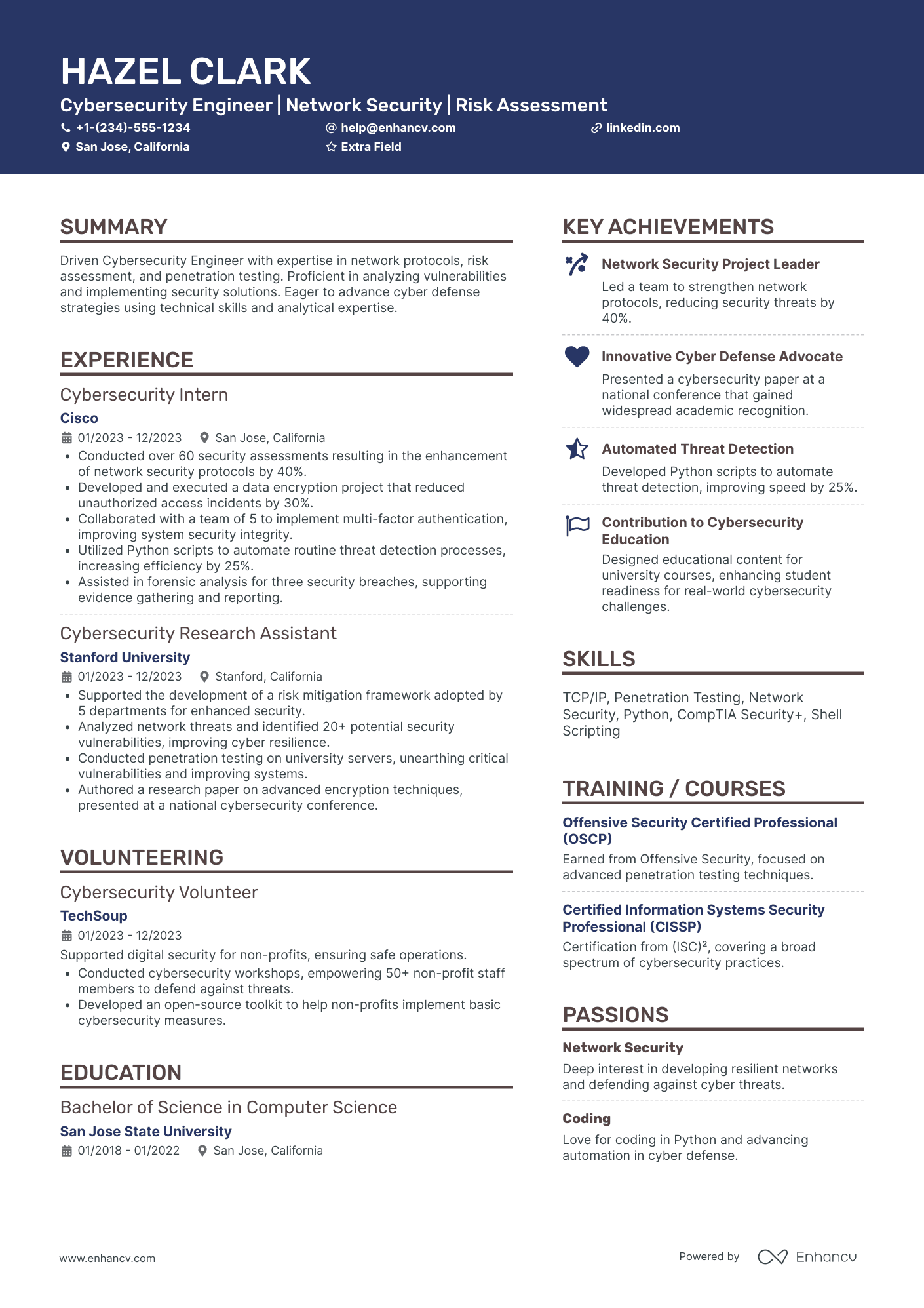
Within the example above, we have
- Certification, years of experience, and quantification of the results achieved
- Technical skills with outcomes and the bigger picture
- Focus on communication style to show character and goals-oriented mindset
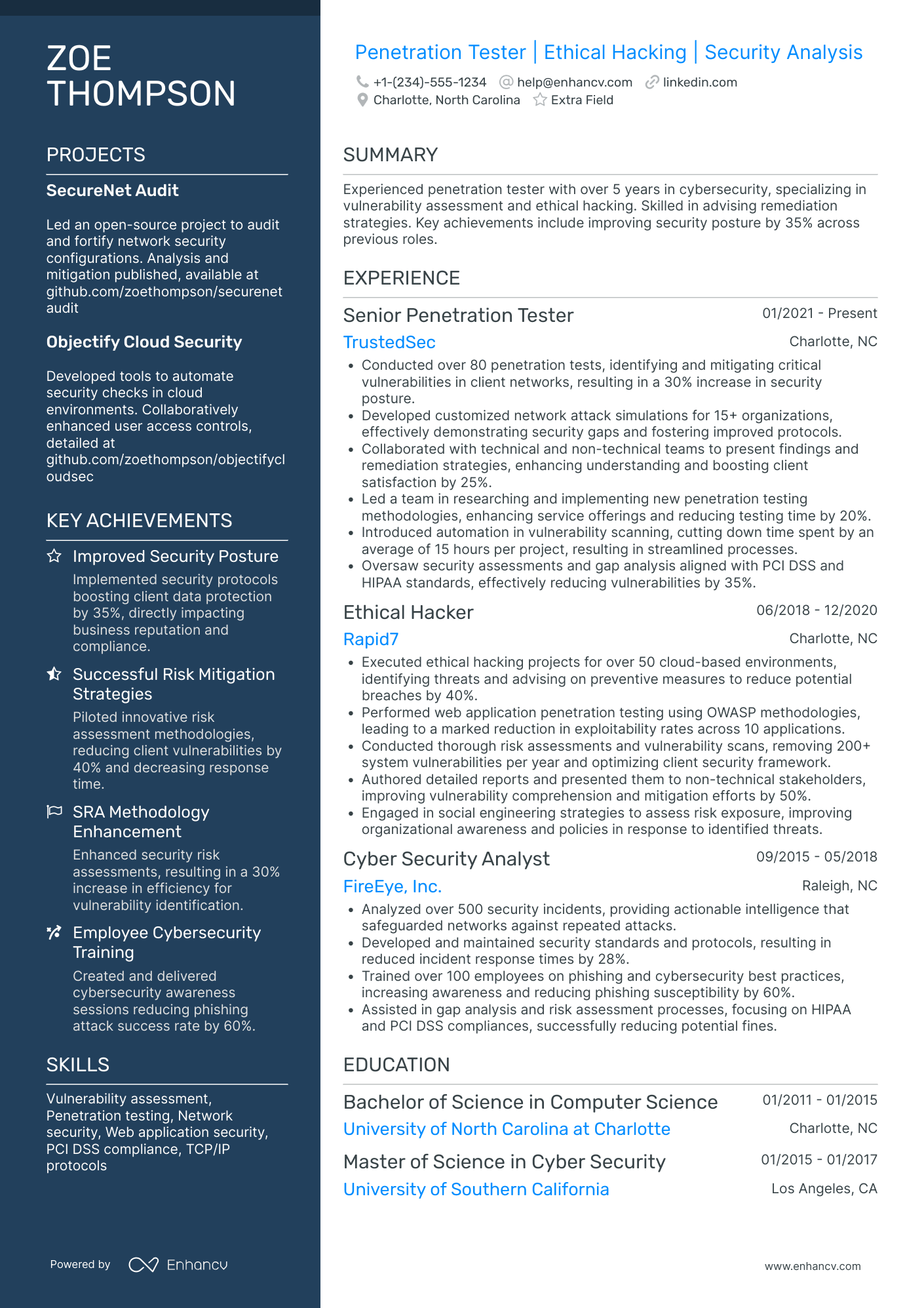
Certified ethical hacker resume experience section
Some CEH think of their experience as a keyword filler to list what they did. The resume experience section serves rather a way more important function.
It's the essence of your resume: answering the question of why organizations should invest in you.
Find below four basic tips and tricks to keep in mind when curating this section.
1. Select only the most relevant experience for the job you're applying for.
Those could include:
- Cyber security responsibilities you've had in the past
- Security consultancy roles (e.g. from the Big Four)
- Technical support or system administrator to show the growth of your experience
2. Select between three and five achievements or outcomes from your experience using particular skills.
On the technological side, it's once again time to consider your experience in auditing the security of:
- computer networks
- operating systems
- internet/ apps
Your resume provides you with an opportunity to show off the vulnerabilities you discovered and how you managed the risks. All within different environments, like Capture The Flag (CTF).
3. Always stick to the formula: "I did this" + "using this technology/ skill" + "the end result was".
You could use the above formula to demonstrate how you communicated security gaps that could lead to potential compromise.
Don't forget to list the different programming languages for a more secure digital environment.
4. Tailor! Tailor! Tailor!
For each job, you apply for. Doesn't matter if it takes more time. Personalization always helps you stand out amongst the pile of CEH resumes.
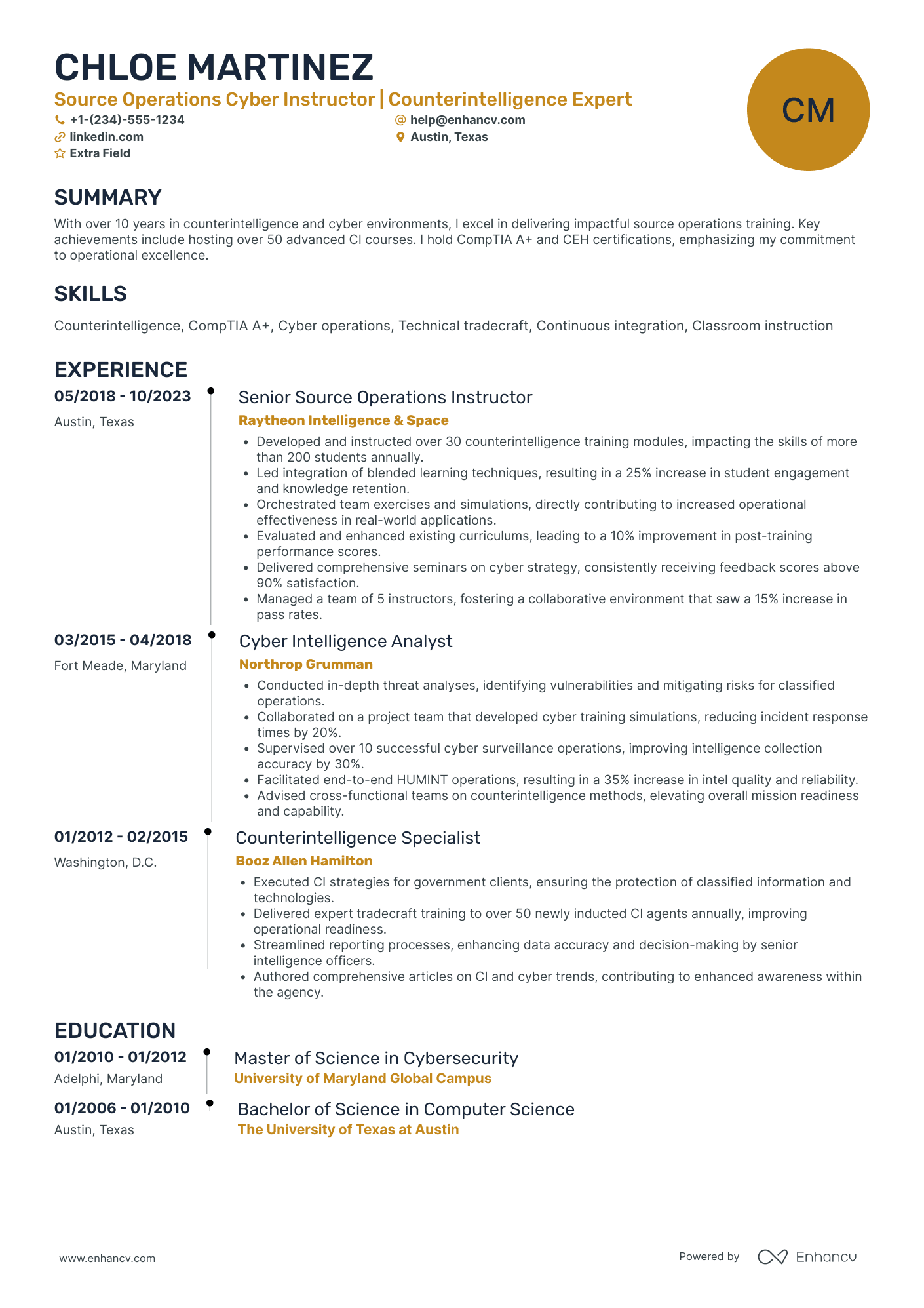
Certified ethical hacker resume experience examples
- •Completed monthly audits
- •Consulted on security
- •Oversaw 120 systems
- •Built cybersecurity strategy
The above experience section just goes on to list items, without any context. It looks sort of like a grocery shopping list - and that’s how it shouldn’t be.
Here’s how you can seize this opportunity to make your resume experience section serve a purpose and showcase why you’re perfect for the role.
- •Completed 5 monthly audits by performing various network and operating systems simulation attacks to find vulnerabilities
- •Consulted on security and patched 150+ security flaws within hybrid employee environment
- •Oversaw and monitored the security of 120 PC and laptops: updating security protocols and firewalls on a bi-weekly basis
- •Built cybersecurity strategy from scratch and tailored to ever-growing organizational needs to achieve an 89% more secure digital environment
The basics of the role still exist within this experience section. But it serves the function to narrate:
- achievements
- skills
- benefits for the organization
That’s what a good experience section should do. But have you ever wondered how to curate your resume if you’re just starting off within the cybersecurity industry?
Entry-level certified ethical hacker resume tips
You dream of becoming a CEH, but your resume experience is feeling pretty light. This next section of our guide will show you how to focus on your skills via a hybrid resume format.
To start off, what recruiters care most about in this industry is certification. Even though some of the certificates may be pretty expensive, they do provide you with a gateway to landing your dream role.
Another item that can open doors for you is your higher education. If you've completed a BS in Computer Science or the like, make sure it's listed on your resume.
Your experience working in technical support is actually pretty relevant to joining a cybersecurity team. As it shows that you're able to communicate, understand complex systems, and solve individual problems. So, make sure you list it on your resume.
Also, think about any relevant internships or research you’ve done. Your “humble” roots show that you’re willing to put in the hours of work to impact the field.
The final most important element to substitute your lack of experience is projects - both personal and professional.
Speaking of your ceh projects
In previous sections of this article, we've noted how important your projects actually are for your certified ethical hacker resume.
Apart from adding your GitHub link to your header, you can create a separate section to highlight some of your biggest achievements.
These could include
- personal projects - systems you've built following instructions or on your own;
- coursework - to demonstrate how you've improved others' projects and applied knowledge to impact the industry;
- isolated virtual labs - where you've repacked malware and understood how an attack works.
Remember that this section needs to be easily comprehensible by all professionals (from Senior Cyber Security Engineers to Non-Technical Recruiters).
Certified ethical hacker most wanted skills
Your CEH resume should curate the right balance between hard or technical skills and soft skills. As these pinpoint the full picture of what type of cybersecurity professional you are.
The hard skills are the obvious ones - the technologies you use (or are apt at using), relevant for the job.
We recommend that you list these within
- separate technical skills and headline sections as keywords;
- summary and experience bullets to showcase what you've achieved;
- projects to dive more in-depth into your expertise.
Just always remember to keep your sections relevant to the job you're applying for.
Here are some technical skills to get the ball rolling:
30+ CEH technical skills list for resumes
- Cyber Security Audits
- NMap and its variants
- Burpsuite
- SQL Map
- Enumeration Tools
- Assembly
- Python
- C Programming (C/C++)
- JavaScript
- R
- Ruby
- Haddock
- Offensive Cyber Security
- Bash
- PowerShell
- SQL
- Memory Management
- Allocators
- System Interference
- Computer Networks
- Network Security
- Network Pen Testing
- Operating Systems
- Statistics
- Linux CLI
- Windows
- Physical Security
- Raspberry Pi
- Web App Testing
- Vulnerability Assessment
- Risk Assessment
- Internet Security and Management
- Bug Bounties
- Security Flaws
- Weaknesses
- Security Exploits
How to describe soft skills on your resume
Even if you've all the relevant certifications, experience, and knowledge - there's one thing that could ruin your chances of landing that CEH role.
Recruiters actually care about your soft skills. Or your abilities to interact with people, resolve problems, and your personal traits.
As nobody wants to hire a robot that can just do the job without actually being able to adapt to the team.
And within CEH, communicating effectively vulnerabilities across different organizational levels is key to the success of the role.
Because you know that you'd present the problems to C-Level executives versus Senior Cyber Security Engineers versus Office Administrators in completely different manners.
Another soft skill at the core of your role is ethics. You need to hold values that support the organizational mission.
Use the strengths or achievements section of your resume to go into further details about your soft skills.
20+ soft skills you don’t want to miss out on on your resume
- Ethics
- Interpersonal communications
- Presentation
- Reporting
- Research
- Auditing
- Persistence
- Stubborn
- Patience
- Work under pressure
- Flexibility
- Monitoring
- Stakeholder Management
- Independent
- Compliance
- Collaborative
- Critical Thinking
- Analytical Thinking
- Strategic Thinking
- Step-By-Step Mindset
- Problem Solving
- Responsibility
- Innovation
- Reliability
- Multi-Tasking
Ceh certificates for resumes
Certificates in cyber security always divide opinions.
Professionals deem that most certification provides a nice entryway to the industry, but isn't self-sufficient.
Recruiters, on the other hand, have them on the top of their "ideal candidate" checklists.
Our advice is to always include any relevant certificates you may have within a separate section and the summary of your resume.
These are a few certificates you can add that are amongst the most popular in the cybersecurity industry.
Top 12 certificates for your resume
- CEH
- OSCP
- CompTIA Net+
- CompTIA Sec+
- CompTIA Pentest +
- CISSP
- SANS
- CISCO CCNA R/S
- CISCO Cyberops
- Redhat CSA
- GPEN
- CREST
Certified ethical hacker education section on a resume
While your education may not be that decisive "make it or break it" element, recruiters would assess your CEH resume based on your higher education.
So, if you have a degree that's relevant to cybersecurity, include it on your resume with the institution and start/end dates.
Examples of relevant degrees include:
- BS in Computer Science
- BS in Information Technology
- BS in Mathematics
- MS in Cybercrime
- MS in Data Science
- MS in Information Security
Key takeaways
- Curate your resume summary to include these five elements: certification, years of experience in the industry, achievements, soft skills, and communication.
- Make sure your experience is relevant to the job you’re applying for and follows the "I did this" + "using this technology/ skill" + "the end result was" formula.
- Use your resume experience to illustrate how you’ve secured networks, operating systems, and web apps in the past.
- Dedicate a separate section to shine a light on your more prominent projects, including coursework and virtual labs.
- Balance both your technical and soft skills to make a lasting impression on recruiters.
Ethical Hacker resume examples
By Experience
By Role