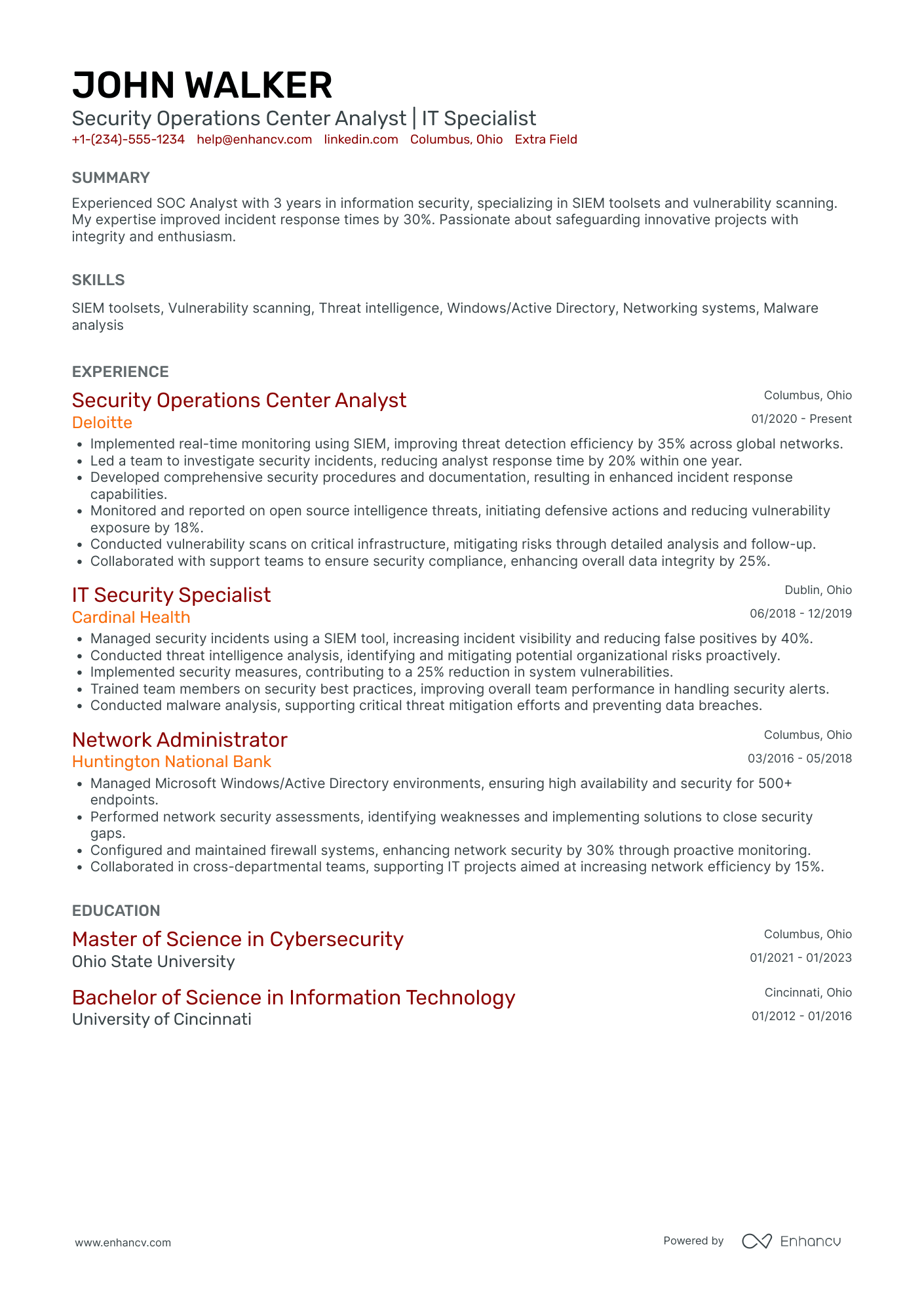
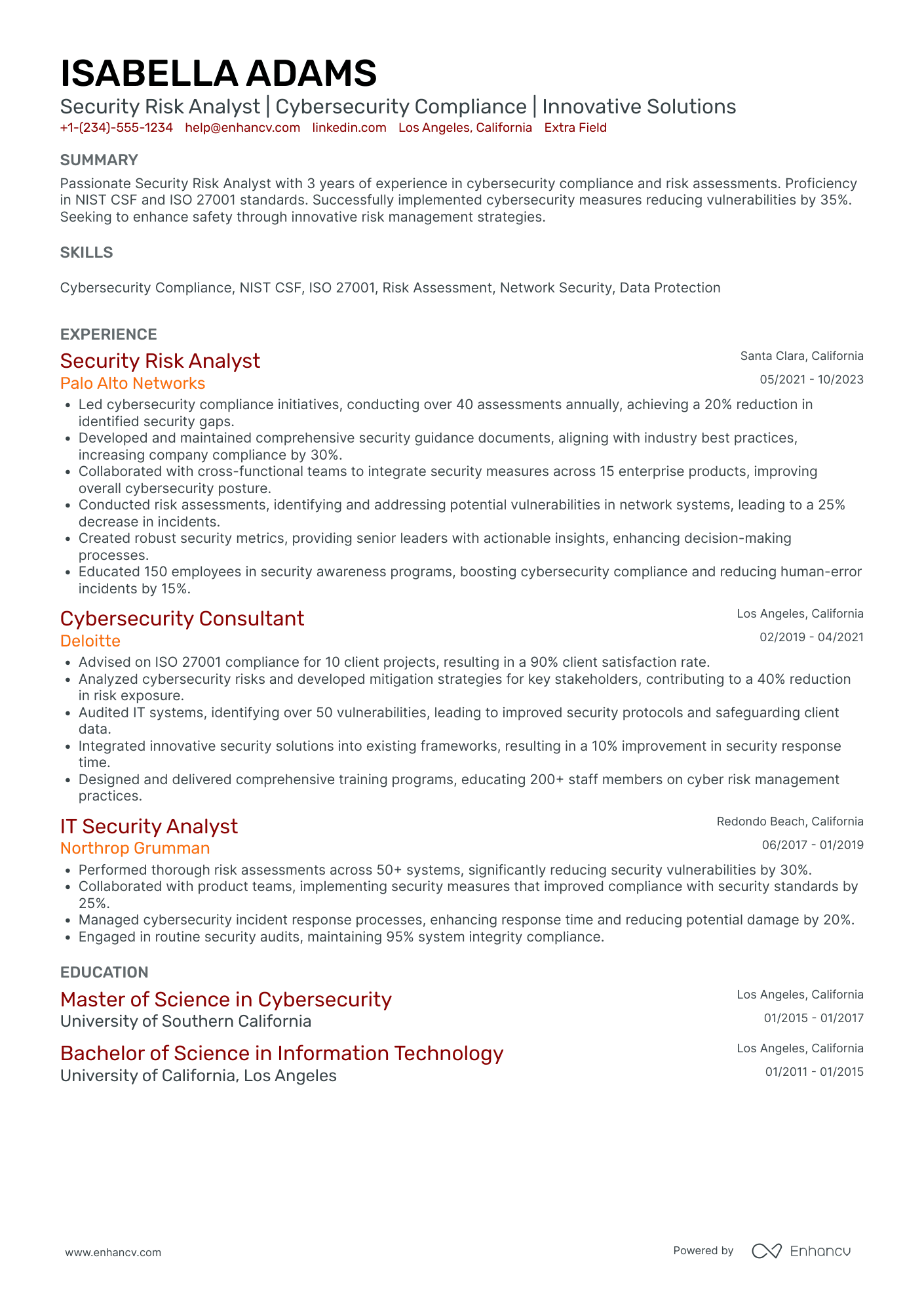
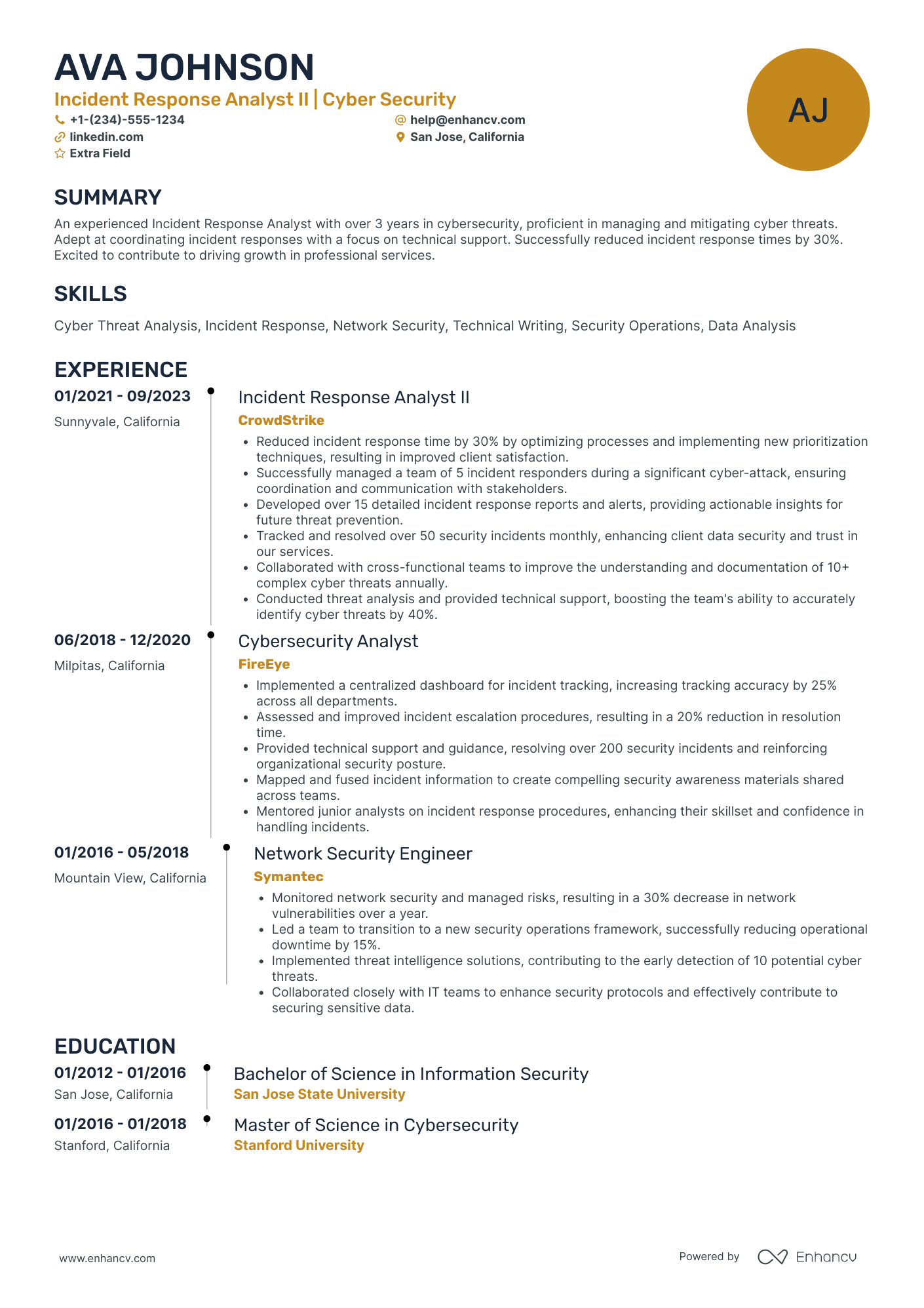
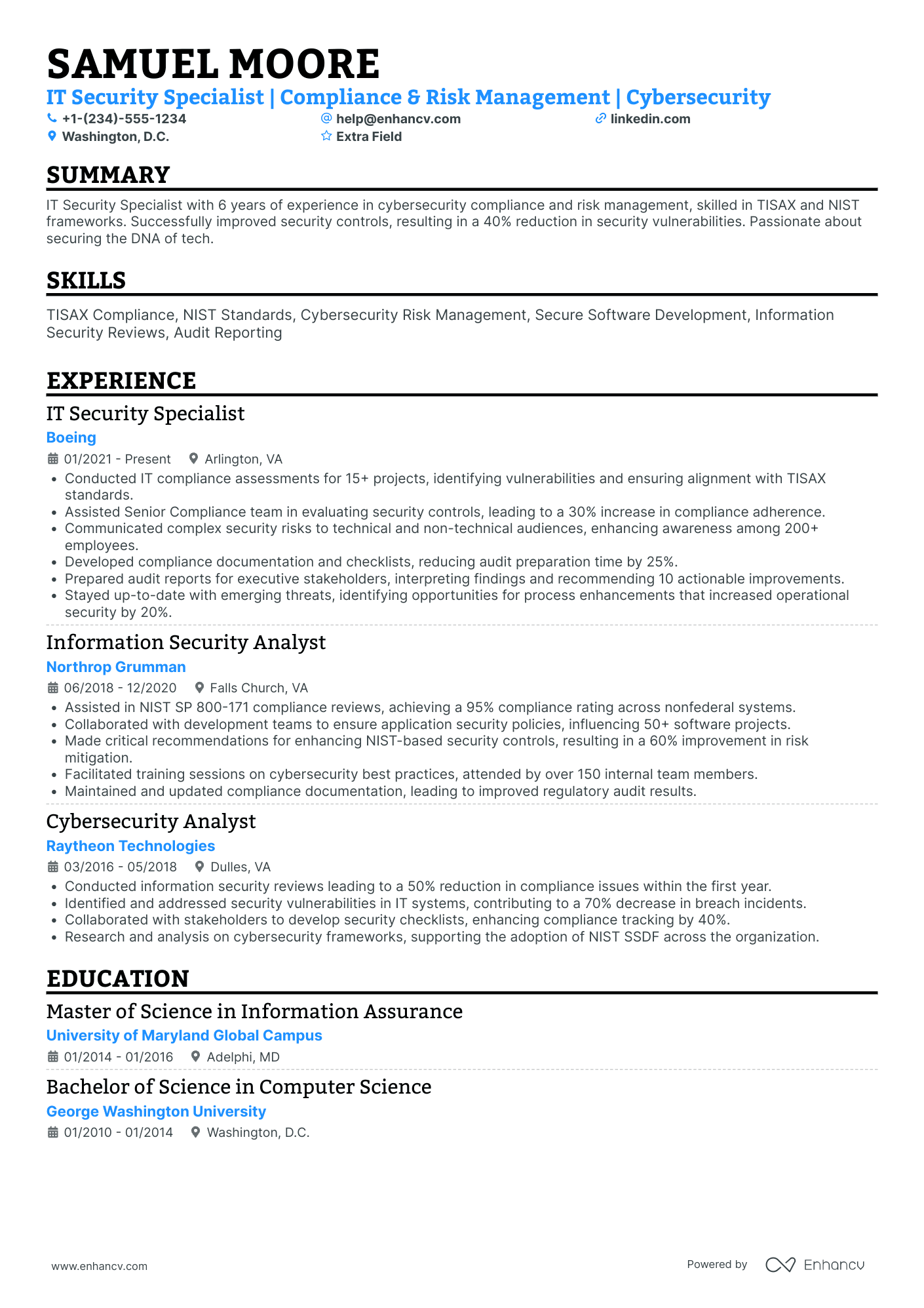
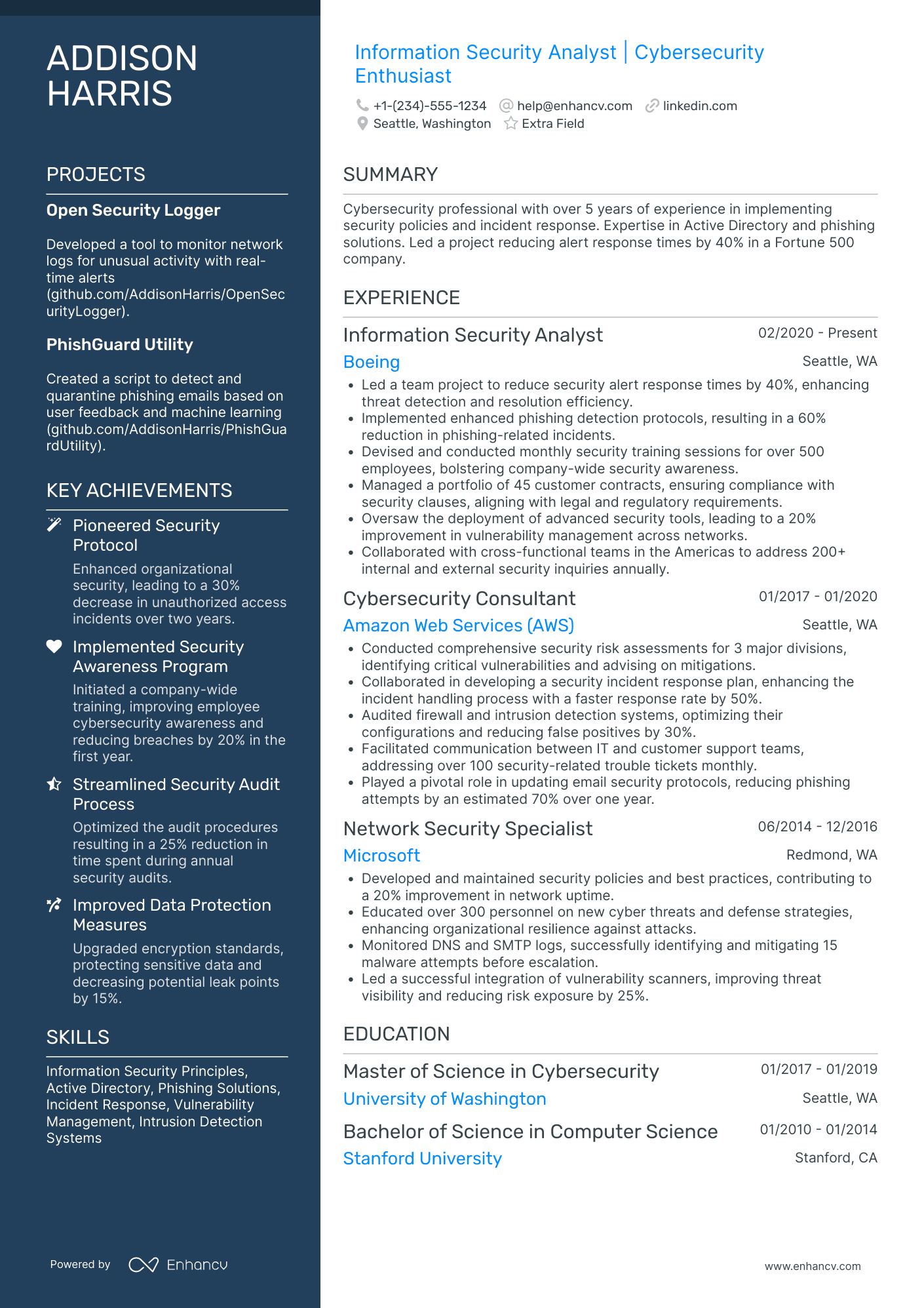
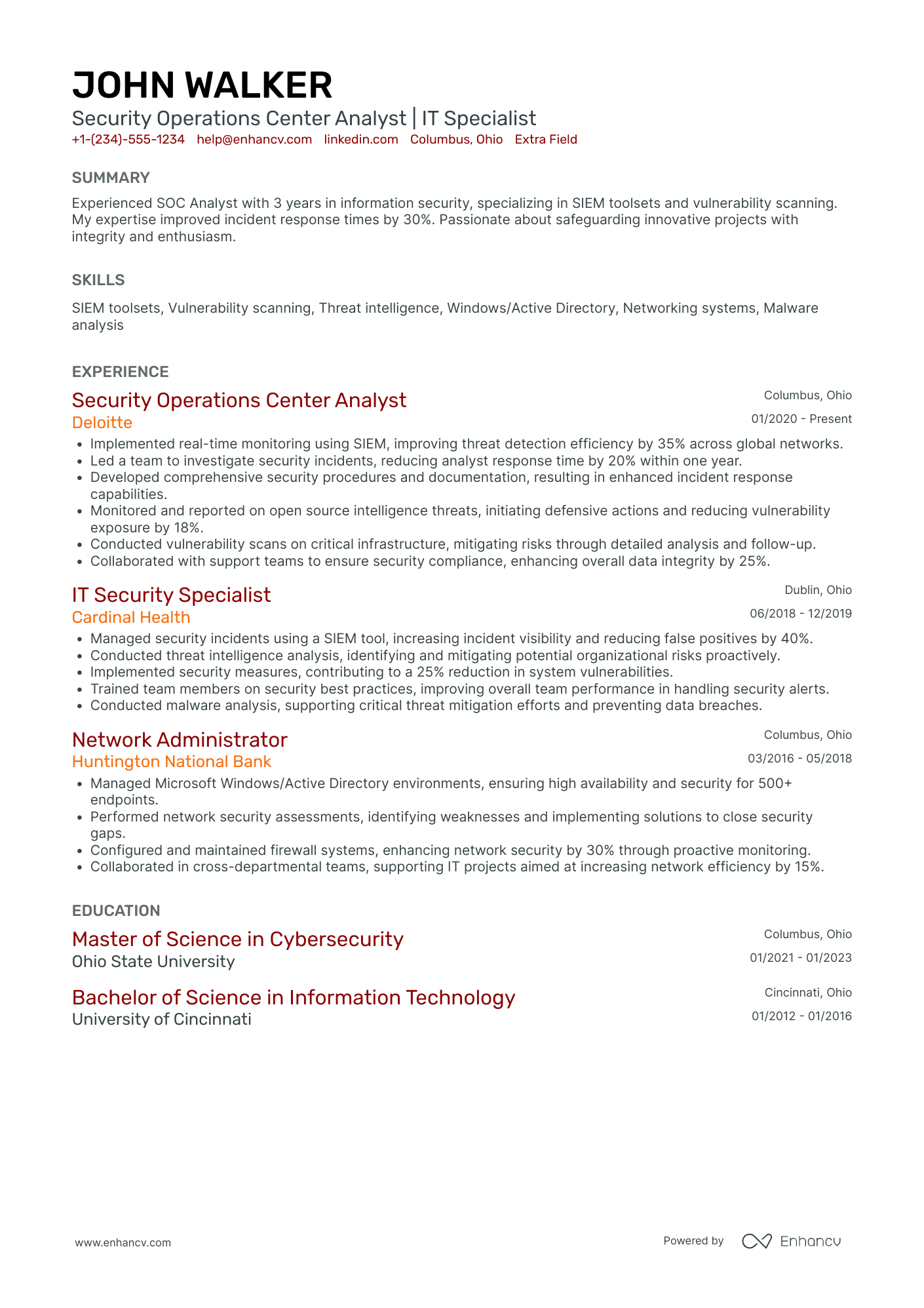
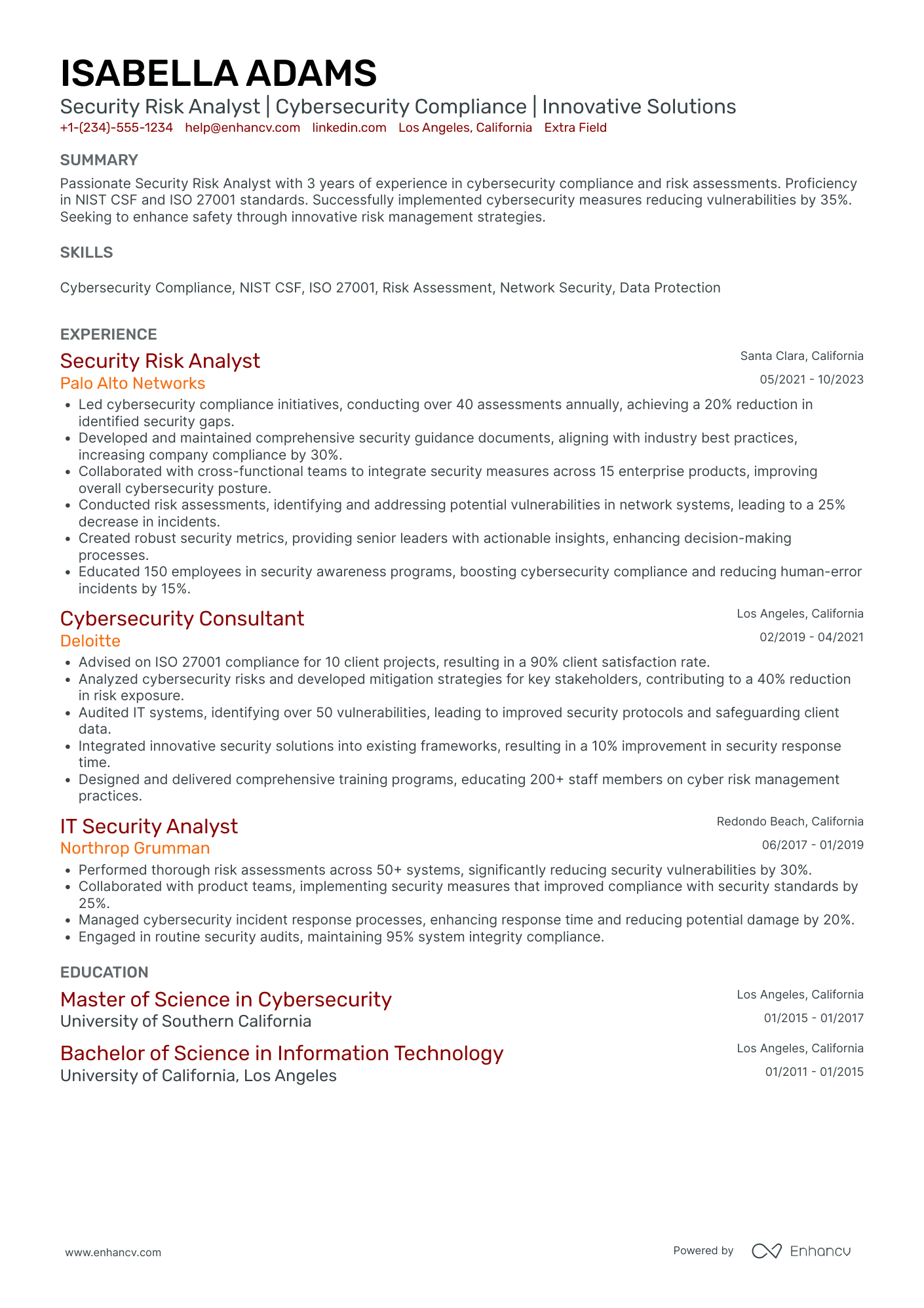
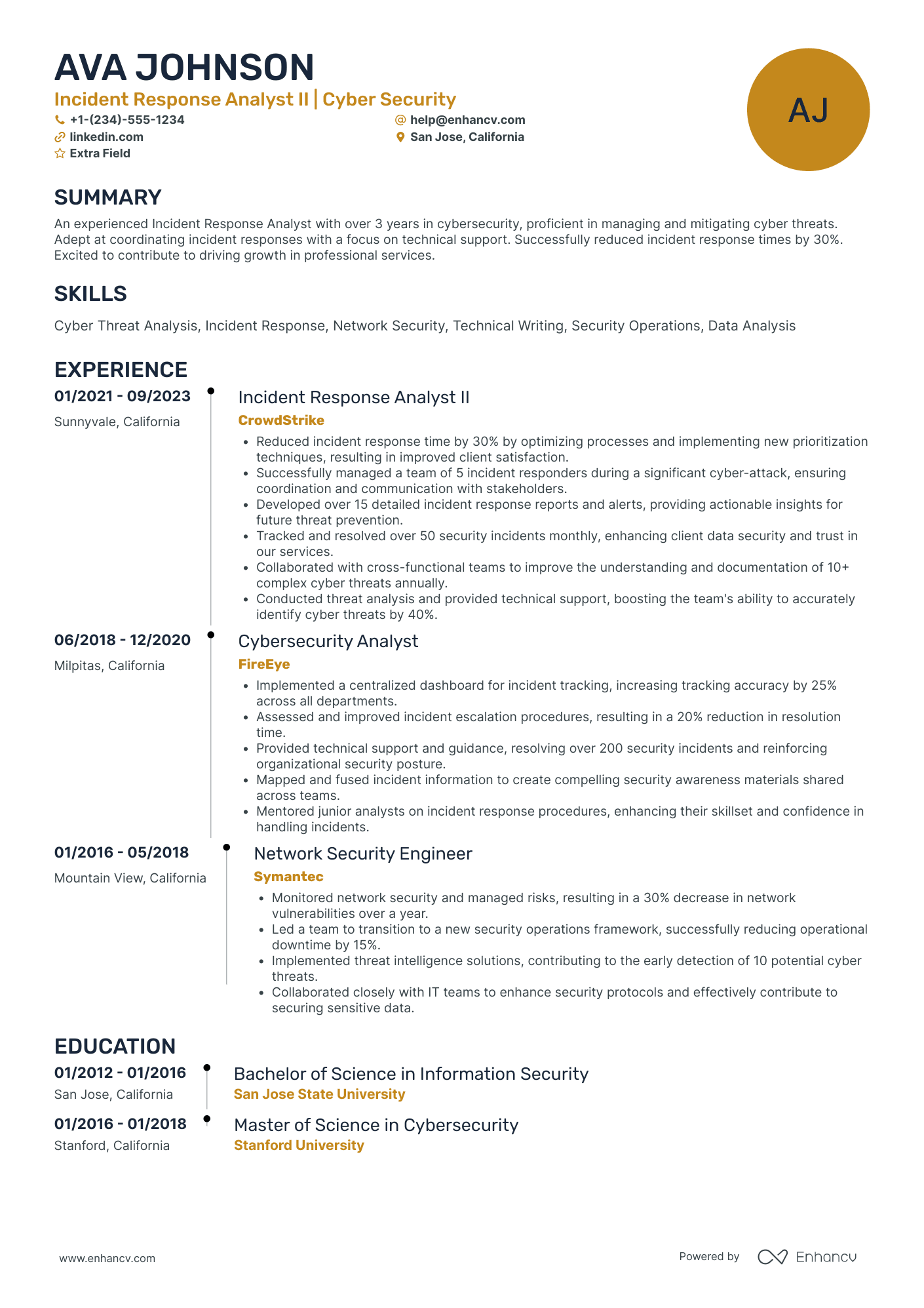
As a security analyst, you’re the frontline that turns alerts into action and threats into lessons learned. Technical chops (SIEM, EDR, SOAR, log hunting, scripting) get you noticed, but what wins interviews is clear evidence of impact: faster containment, fewer false positives, and measurable reductions in business risk.
According to the U.S. Bureau of Labor Statistics, as of November 2025, employment for information security analysts is projected to grow 29% from 2024 to 2034. Such a growth rate is much faster than average. It means security IT roles will be in demand but it will be harder to land a high-profile position.
To stay competitive, your resume should show both forensic depth and strategic thinking: how you improved detection coverage, tightened controls, shortened MTTD/MTTR, or made audits painless. In this guide, we’ll show you how to build a Security Analyst resume that leads with outcomes.
Key takeaways
- Use reverse chronology to show a clear timeline in IT security.
- Think like a responder, keep bullets concise, action-first, and impact-driven.
- Describe how you improved detection, containment, and risk posture.
- Use metrics like MTTD, MTTR, and false-positive rates.
- Mirror the exact tools from job descriptions (e.g., Splunk, XSOAR), align with metrics (e.g., alerts/day, endpoints), and reference frameworks (MITRE, SOC 2).
- Prioritize relevant certifications (e.g., GCIH, Security+).
- List hands-on projects to show technical readiness if you’re junior.
Let’s go over various security analyst resumes and see what makes them compelling.
Resume examples
By Experience
Junior Security Analyst
- Focus on showing transferable skills. Detail any scripting or basic coding projects (e.g., Python, PowerShell) that automate simple tasks.
- Lab environment experience is useful. List specific Capture The Flag events, successful completion of platforms like TryHackMe or Hack The Box, or personal home lab setups.
- Show eagerness to learn. Mention specific, in-progress certifications (e.g., Security+, CySA+).
Senior Security Analyst
- Detail achievements like reducing security incident recurrence or saving the company money by optimizing existing security tools.
- List experience in implementing a major security technology stack (e.g., SIEM, SOAR, EDR) across the enterprise.
- Include bullet points mentioning training junior staff, leading incident after-action reviews, or serving as a subject matter expert for cross-functional teams.
By Role
Cyber Security Analyst
- Specify your security tool proficiency by mentioning which specific SIEM (e.g., Splunk, QRadar) you've created custom dashboards or correlation rules for.
- Mention direct experience implementing controls for specific standards like NIST CSF, ISO 27001, or SOC 2, to show knowledge of regulatory frameworks.
- Reference specific actions taken within a major cloud platform (configuring AWS or Azure Network Security Groups).
IT Security Analyst
- Focus on your experience managing and securing foundational IT services, specifically listing skills in Active Directory/Azure AD hardening, Group Policy, and Identity and Access Management (IAM).
- Detail your involvement in securing core infrastructure components, such as managing security settings for VPNs, proxies, and virtualization environments (e.g., VMware, Hyper-V).
- Showcase your ability to handle diverse security tasks by describing work that spanned different domains, from managing firewall rules to administering antivirus/anti-malware solutions.
Cloud Security Analyst
- Detail your expertise in managing native cloud security tools across specific platforms (e.g., configuring AWS GuardDuty and Security Hub, or Azure Security Center).
- Emphasize your role in implementing and managing IaaS/PaaS security controls and leveraging Infrastructure as Code (IaC) tools like Terraform to define security policies.
- List experience with CSPM (Cloud Security Posture Management) tools and how you used them to ensure continuous compliance and remediate misconfigurations in cloud environments.
Data Security Analyst
- Detail specific rule sets or policies you've engineered to protect regulated data, such as PII or PHI.
- List the technologies you used for data-at-rest or data-in-transit encryption, like hardware security modules or key management service.
- Show experience with data discovery and classification tools by mentioning the specific products you used.
Threat Intelligence Security Analyst
- Detail experience with specific threat intelligence platforms such as MISP or Anomali and describe how you used them.
- Show your report writing and communication skills by referencing specific examples of producing threat briefs.
- Describing how you mapped specific threat groups or incidents to relevant techniques and developed proactive defenses based on that mapping.
Network Security Analyst
- List specific deep-level networking protocols (e.g., BGP, OSPF, MPLS) you have configured security policies around.
- Detail experience with specific IDS/IPS platforms and your ability to write custom signatures to detect zero-day or targeted threats.
- Show advanced segmentation skills by describing projects where you implemented Zero Trust architectures or micro-segmentation.
Endpoint Security Analyst
- Focus on specific Endpoint Detection and Response tools like CrowdStrike, SentinelOne, or Microsoft Defender for Endpoint.
- List experience with operating system hardening by detailing specific security baselines (e.g., CIS Benchmarks).
- Mention platforms like Intune or Workspace ONE and your role in enforcing security policies on mobile endpoints.
Information Security Analyst
- Describe your involvement in drafting, reviewing, or disseminating company-wide security policies, standards, and guidelines.
- Detail specific GRC tools you've used for policy mapping, control testing, or managing audit evidence (e.g., ServiceNow GRC, LogicManager).
- Mention successful initiatives you led to improve employee security posture (e.g., reducing phishing click rates by X%).
Vulnerability Assessment Security Analyst
- Show experience with configuration management tools like Ansible or Puppet and how you used them to automate the fixing of non-patchable configuration vulnerabilities.
- List specific commercial and open-source vulnerability scanners (e.g., Nessus, Qualys, OpenVAS) you've configured..
- Mention specific systems (e.g., SCCM, WSUS, BigFix) and how you prioritized critical vulnerabilities for remediation based on CVSS scores and exploitation risk.
Security Operations Center (SOC) Analyst
- Emphasize your triage and investigation skills by mentioning the average time you reduced incident response time by.
- List experience with Security Orchestration, Automation, and Response playbooks and whether you've created, optimized, or executed them to automate repetitive security tasks.
- Mention specific services you’ve onboarded into the SIEM and the parsing rules you developed for them.
Risk Management Security Analyst
- State which frameworks (e.g., FAIR, Octave) you have experience applying to business assets.
- Describe how you evaluated vendor security postures using platforms like ServiceNow or by reviewing SOC 2 reports and questionnaires.
- Detail how you translated technical security findings into clear, financially-backed risk metrics and recommendations for senior management.
Forensic Security Analyst
- List specific forensic tools and operating systems you are expert in, such as EnCase, FTK, Autopsy, or CAINE.
- Write about your experience maintaining legal admissibility for digital evidence and presenting findings in formal investigative reports.
- Describe experience using tools like Volatility to analyze memory dumps for evidence of malware infection or advanced threat execution.
Application Security Analyst
- Detail experience with specific static and dynamic analysis tools (SAST/DAST) such as Checkmarx, Veracode, or Acunetix.
- Mention your ability to translate security findings into actionable remediation advice for development teams using platforms like JIRA.
- Describe specific projects where you actively tested for and helped remediate high-risk application vulnerabilities like Injection flaws or Insecure Design. This way you show deep knowledge of the OWASP Top 10.
Incident Response Security Analyst
- List hands-on experience with specific malware analysis techniques (e.g., sandbox execution, static/dynamic analysis).
- Mention your role in tabletop exercises or simulations involving major incidents like ransomware or significant data breaches.
- Describe the steps you took to isolate infected systems across diverse environments (e.g., cloud, on-prem, mixed OS).
Compliance Security Analyst
- Detail your role in successfully completing an external audit for major compliance frameworks like PCI DSS, HIPAA, or GDPR.
- Focus on how you identified deficiencies between current security controls and mandated regulatory requirements.
- List specific documentation systems or repositories you managed to streamline the compliance reporting process.
Penetration Testing Security Analyst
- Detail experience with niche testing methodologies beyond standard web/network penetration tests, such as red teaming, social engineering, or physical security assessments.
- List specific, custom tooling or scripting you've developed for offensive security operations (e.g., customized exploit code, enumeration scripts in Python/Go).
- Show advanced post-exploitation techniques by mentioning skills like lateral movement or credential harvesting.
Does your current resume look like any of these examples? And what are its weaknesses? Use Enhancv’s ATS Resume Checker to get a full report.
Is your resume good enough?
Drop your resume here or choose a file. PDF & DOCX only. Max 2MB file size.
What resume format works best for a security analyst?
Use a reverse-chronological resume if you’ve done recent SOC/DFIR or engineering work.
Use a hybrid format if you’re junior or pivoting.
How to structure your content
Prioritize work and projects from the last two to three years:
- Underline incidents handled, detections shipped, or controls you hardened.
- Group tools by function—SIEM, EDR, cloud, vuln management—and map them to results(coverage, MTTR, audit findings).
- Set clear dates to underscore chronology (e.g., “Jun 2021 - Apr 2024”).
What sections should go on a security analyst’s resume?
- Resume header (name, cert post-nominals, location, phone, email, LinkedIn, GitHub)
- Professional summary (years in security, SOC tier or role, two quantified outcomes, two core strengths)
- Work experience (a few bullet points per job, each describing scope, tech, and impact)
- Skills (concise, scannable, focused on technical capabilities)
- Education (degree, institution, graduation year, GPA if above 3.5)
- Certifications (only list certs you hold, prioritize recently earned ones or those requested in job ads)
- Projects & Labs (very helpful for juniors and detection engineers)
Now that we covered how your resume should be structured, let’s move on to how you should write it.
How to write your security analyst resume experience section
Write experience bullet points like mini incident reports—action + tool + scope + measurable outcome—and prefer active S–V–O.
Good example of a security analyst experience section
Security Analyst | Horizon Data Systems, Austin, TX
June 2019–Present
- Managed detection for ~1,800 endpoints, cutting false positives by 45% and MTTD from 2.5h to 28m.
- Built 16 SOAR/Sigma playbooks for phishing & lateral movement, saving 150 analyst-hours/month and cutting P1 MTTR from 90m to 22m.
- Hardened AWS (CloudTrail, GuardDuty, IAM); enforced least-privilege and alerts, eliminating an exfiltration channel and reducing privileged anomalies by 67%.
- Led quarterly vulnerability assessments and patching with DevOps, cutting critical backlog by 78% and aiding SOC 2 attestation.
- Mapped detections to MITRE ATT&CK and hunted EDR/cloud logs; discovered credential-theft activity and contained 23 compromised accounts.
- Mentored 4 junior analysts and authored runbooks/triage guides, raising first-touch resolution to 62% and improving incident handovers.
Why does this experience section work?
Security experience is judged by measurable outcomes. Focus your bullets on credential abuse, vulnerability exploitation, and ransomware.
Map your actions to these patterns:
- How many incidents you remediated
- How quickly you detected and contained threats
- How you made the environment measurably safer
PRO TIP
If a job explicitly mentions tooling or frameworks (e.g., Splunk, Sentinel, CrowdStrike, MITRE), surface those early. Put them in your summary and prove them in metric-driven bullets in your experience section.
The most common breach drivers in 2025 were:
- Vulnerability exploitation reached 20% of initial access ( 34% YoY)
- Ransomware appeared in 44% of breaches
- The human element remains ~60%
How to quantify your impact as a security analyst
Pick two or three metrics per role and label scope and time. Numbers оn your resume help hiring managers understand risk reduction or time saved.
Metrics that matter most for security analysts include:
- Detection coverage: % of ATT&CK techniques covered or rules/playbooks deployed (e.g., “+17 Sigma rules; T1059, T1110 covered”).
- MTTD/MTTR: Mean time to detect/respond for P1/P2 incidents over a quarter.
- Vulnerability risk: % critical CVEs remediated within SLA; median days-to-patch on edge/VPN devices. (DBIR notes rising vulnerability exploitation—aim to show patch cadence.)
- Cost/risk impact: Tie wins to IBM’s benchmark (As of July 2024, average breach costs are $4.88M)
- Signal quality: False-positive rate, alert-to-case conversion, or suppressed noisy rules.
- Automation: Tickets auto-enriched/resolved per week; manual minutes saved per alert.
When quantifying your experience, use an action verb, a tool/tech, and a measurable outcome.
Here’s how:
How to quantify achievements on your resume
| How to quantify | Example bullet point |
|---|---|
| MTTD (Mean Time to Detect)—average time to surface a confirmed threat. | “Cut average MTTD from 2.5h to 28m by deploying new Splunk detections and scheduled threat hunts.” |
| MTTR (Mean Time to Remediate/Contain)—average time from detection to containment/remediation. | Automated containment with XSOAR + CrowdStrike, reducing P1 MTTR from 90m to 28m. |
| False-positive rate—percent of alerts identified as non-threats after triage. | Tuned Splunk rules and enrichment, lowering false positives by 38% and improving analyst focus. |
| Alerts to cases conversion—proportion of raw alerts that become investigated incidents/cases. | Triaged over 1,200 alerts/week, increasing alerts to case conversion from 4% to 11%. |
| Analyst-hours saved—time reclaimed via automation, playbooks, or detection tuning. | Built 8 SOAR playbooks that automated enrichment/containment, saving over 120 analyst-hours/month. |
Need help with quantifying your experience? With Enhancv’s AI Bullet Point Generator, you can quickly turn regular security analyst tasks into metrics-driven statements.
Now that you understand how to write your experience, let’s make it even more compelling to employers.
How to tailor your security analyst resume experience
To create a targeted resume, mirror the employer’s language (tools, scale, metrics, and responsibilities) while keeping your bullets truthful and outcome-focused.
Here’s how:
- Use exact tool names and versions the ad lists (e.g., Splunk, Microsoft Sentinel, CrowdStrike Falcon, Cortex XSOAR). ATS often matches exact tokens.
- Match scope/scale they advertise: endpoints, users, cloud accounts, log sources, alerts/day, SOC tier. If the ad says “50k endpoints,” show the endpoints you covered.
- Speak their metrics: if they measure MTTR, false positives, or alerts→cases, use those metrics in your bullets.
- Map to frameworks they care about (MITRE ATT&CK, NIST CSF, CIS controls, PCI, SOC 2) and call out the artifact (e.g., “mapped to ATT&CK” or “aligned to NIST CSF”).
- Mirror the function words they use: “threat hunting,” “detection engineering,” “IR,” “SOAR playbooks,” “vulnerability remediation.” Use the same verbs and nouns.
- Describe deliverables the employer values: playbooks, Sigma/KQL rules, incident reports, tabletop exercises, automated containment steps, and IOC lists.
Job description from a real posting
We’re hiring a Security Analyst to defend a hybrid environment made up of AWS and on-prem datacenters. You’ll monitor and investigate security telemetry, create and tune detection rules and automated playbooks, and drive incident response to meet aggressive MTTD/MTTR goals. Script automation (Python or PowerShell) to accelerate containment, run proactive threat hunts across cloud and endpoint logs, and help map incidents to frameworks for audits and compliance. Experience with SIEM and EDR platforms and familiarity with MITRE ATT&CK, SOC 2, or NIST is preferred.
Here’s how to tailor bullet points for each of the highlighted requirements.
Resume tailoring examples for security analysts
| Job description excerpt | Untailored bullet | Tailored bullet |
|---|---|---|
| “Monitor and investigate security telemetry.” | Monitored security telemetry and investigated alerts. | Monitored Splunk and EDR telemetry across ~40k endpoints; triaged ~2k alerts/day and escalated confirmed incidents, reducing false positives by 38%. |
| “Develop and tune detection rules and automated playbooks.” | Wrote detection rules and built automated playbooks. | Authored 12 SPL/KQL detection rules and 8 Cortex XSOAR playbooks to automate enrichment/containment for phishing and lateral movement, saving ~120 analyst-hours/month. |
| “Meet MTTD/MTTR SLAs across corporate systems.” | Worked to meet MTTD and MTTR targets. | Tuned detections and automated containment to cut average MTTD from 2.5h → 28m and bring P1 MTTR < 30m, meeting SOC SLAs. |
| “Experience with automation and scripting (Python or PowerShell).| | Automated repetitive tasks using scripting. | Built Python/PowerShell automation that auto-quarantined infected hosts via EDR and updated blocklists, reducing containment time by ~65%. |
| |Threat hunting, cloud logging, and mapping to frameworks (MITRE, SOC 2, NIST).” | Performed threat hunts and supported audits. | Conducted proactive hunts across CloudTrail and EDR logs, mapped findings to MITRE ATT&CK, and closed 6 audit-relevant gaps used in SOC 2/NIST evidence. |
PRO TIP
Use Enhancv’s One-Click Tailoring Feature to automatically match your bullet points, skills, and sections to any job description.
After all these efforts, your experience is presented in the best possible light. Now, let’s move on to another resume section essential for this role.
How to list technical skills on a security analyst resume
Technical skills help recruiters and ATS instantly spot whether you can do the job.
Here’s where to place skills on your resume:
- Experienced analysts (Tier 2–3, DFIR, detection engineers): Put a targeted technical skills block after your work experience. If you’re using a double-column resume, then you can put it parallel to your experience.
- If you have many skills relevant to the role: Group them by category (SIEM/EDR/Automation/Cloud/Forensics) so the ATS can parse them correctly.
Best technical skills for your security analyst resume
- SIEM: Splunk, Microsoft Sentinel, QRadar, LogRhythm
- EDR: CrowdStrike, Microsoft Defender, Carbon Black
- SOAR/automation: Cortex XSOAR, Phantom, Demisto, Python, PowerShell
- Detection languages: SPL, KQL, Sigma rules, YARA
- Cloud logging & security: AWS CloudTrail, CloudWatch, Azure Monitor, GCP Audit Logs
- Forensics & IR tools: Volatility, GRR, FTK, Autopsy, Wireshark, Zeek
- Threat hunting & analytics: TTP mapping (MITRE ATT&CK), IOC development, telemetry analysis
- Vulnerability & posture: Nessus, Qualys, Tenable, vulnerability remediation workflows
- Networking & protocols (useful): TCP/IP, DNS, proxy logs, firewalls (conceptual)
- Compliance & frameworks: NIST CSF, CIS Controls, SOC 2 evidence gathering
How to integrate soft skills on a security analyst resume
Weave them into your summary, experience bullets, and project descriptions, always tied to a measurable result or clear deliverable.
Here are some examples.
Summary:
“Skilled communicator who keeps teams aligned and calm during high-pressure incidents.”
Experience bullet:
“Coordinated with IT and Legal to ensure smooth, collaborative incident response.”
Project description:
“Led a tabletop exercise, fostering open feedback and teamwork across departments.”
Soft skills in IT security aren’t a separate “nice-to-have” block. They’re evidence of how you get things done under pressure.
Best soft skills for your security analyst resume
- Clear incident communication (to engineering and executives)
- Cross-team coordination and escalation
- Rapid decision-making under pressure
- Runbook & playbook authorship
- Teaching/mentoring junior analysts
- Analytical problem solving
- Attention to detail
We covered your experience and technical capabilities—now let’s back them up with some credentials.
How to list certifications and credentials on a security analyst resume
Certifications take priority on an IT resume. They're a high-signal readiness for security roles.
List each one with:
- Full certification title
- Issuing organization
- Year obtained (add “current” or expiration if required by the employer)
Certification entry sample:
CompTIA Security+ — CompTIA, 2025
GIAC Certified Incident Handler (GCIH) — SANS, 2025
Quick tips:
- Put certifications near the top if the job prioritizes them (or you’re career changing).
- Include vendor-region specifics when relevant (e.g., “AWS Security Specialty — AWS”) to match job requirements.
- For expiring certs, note the year and status (e.g., “Active,” “Recertified 2024”).
- Keep entries short, factual, and verifiable.
If you completed security-relevant bootcamps, CTF rankings, or SANS courses, include them in a Projects or Professional Development section rather than as formal certs.
Best certifications for your security analyst resume
How to list education on a security analyst resume
Keep education concise so recruiters can see you’ve got the educational foundation for the industry.
What to include in your education section:
Education entry sample
Bachelor of Science in Cybersecurity | Georgia Institute of Technology, 2019
Associate of Science in Computer Science | Austin Community College, 2016, GPA: 3.7
If you’re early in your security career, expand the education section with relevant coursework or capstone projects (e.g., Incident Response, Digital Forensics, Cloud Security, Network Defense, Secure Coding).
When you’re done writing the bulk of your resume, it’s time to write the introduction of your professional persona.
How to write your security analyst resume summary
Keep your resume summary concise, confident, and outcome-focused so hiring managers instantly see your operational impact.
A strong security analyst resume summary includes:
- Current role and years of experience
- Environment type or specialization (SOC tier, cloud, enterprise, DFIR, detection engineering)
- Key tools and techniques (SIEM, EDR, SOAR, threat hunting, scripting)
- One to two quantified results (MTTD/MTTR improvement, false-positive reduction, analyst-hours saved)
- Soft skills tied to outcomes
Example summary
Collaborative security analyst with 5+ years in Tier-2 SOC protecting hybrid cloud and enterprise environments. Skilled in Splunk, Microsoft Sentinel, CrowdStrike, and XSOAR; authored detections and automated playbooks that cut MTTD from 2.5h to 28m and reduced false positives by 38%. Known for clear incident communication, cross-team leadership, and mentoring junior analysts to improve response quality.
Why this summary works:
- Establishes experience level, security specialization, and hands-on use of industry tools.
- Demonstrates measurable impact with concrete security outcomes.
- Show technical depth, business value, and interpersonal skills.
Get a resume summary that shows you can lead and deliver
Drop your resume here or choose a file.
PDF & DOCX only. Max 2MB file size.
What about if you’re early in your career and you’re just starting your professional journey in IT security?
How do I write a security analyst resume with no experience?
You can build a persuasive security resume without years in a SOC by proving technical readiness and investigative thinking.
Shift the focus to coursework, certs, and hands-on labs/CTFs so hiring managers see a foundation of technical skills and motivation.
What to include instead of full-time security analyst experience
- Certifications: List the most relevant ones right after your summary.
- Academic projects or labs: Describe simulated IR exercises, SIEM searches you wrote, or hosted ELK/CloudTrail log pipelines used for hunts. Mention tools (Splunk, Sentinel, CrowdStrike, Volatility, GRR).
- Internships/IT support roles: Highlight triage, ticket handling, basic forensics, and escalation—these show transferable incident-handling experience.
- Personal/homelab projects: Note threat-hunt writeups, detection rule repos (Sigma/SPL/KQL), EDR playbooks, or Python automation that quarantined test hosts.
- Volunteer work: Include pro-bono assessments, SOC help for nonprofits, or running security workshops—demonstrates initiative and real-world impact.
Now that we’ve covered the essential components of a resume, it’s time to fine-tune some of the details.
Frequently asked questions for security analyst resumes
Here’s some clarity around common concerns applicants have.
What design and text formatting rules should you follow for a security analyst resume?
In short, keep your resume professional and ATS-friendly:
- Use one-inch margins, single spacing, and a 10-12 pt resume-friendly font (Arial, Rubik, Montserrat).
- Subtle accent color is acceptable. Avoid heavy graphics and icons that can break ATS parsing.
- Use clear section headings and simple separators (bullets, commas).
How should you name and save your resume file?
Use a clear filename so recruiters and ATS can find it easily.
Example: Henry_Steinberg_Security_Analyst.pdf
Export as a PDF file to preserve layout and prevent font/format shifts across systems.
What should a security analyst cover letter include?
Use the cover letter to tell one concise, relevant incident story that connects your hands-on work to the employer’s needs.
Focus on:
- Why do you want to work for this organization or on this tech stack?
- A short incident vignette (detection, your role/actions, tools used, measurable outcome).
- How you’ll apply that experience to their environment (SIEM, EDR, cloud, compliance).
Keep it one page and targeted—don’t repeat the resume.
Drop your resume here or choose a file.
PDF & DOCX only. Max 2MB file size.
How do I show career progression on a security analyst resume?
Chronology and metrics make career progression evident on IT resumes.
- Use reverse-chronological order so promotions and ownership are visible.
- Show scope increases (endpoints, alerts/day, log sources, cloud accounts).
- Call out new responsibilities (IR lead, detection engineering, playbook ownership).
What additional sections work well on a security analyst resume?
Stick to sections that substantiate your IT security skills:
- Projects: Playbooks, detection rules, threat-hunt reports, automation scripts.
- Open-source/epos: Sigma/SPL/KQL rules, GitHub detection libraries, SOAR playbooks.
- CTF/competitions: Notable placements or relevant challenges.
- Presentations/publications: Talks, blog posts, or whitepapers on IR/detection.
- Clearance/legal: Active security clearance or jurisdiction-specific notes (if applicable).
Do I need specific certifications to work as a Security Analyst in the U.S.?
Not legally required, but many employers expect or prefer certs that show practical detection/IR ability (e.g., Security+, CySA+, GCIH, Splunk/Sentinel certs).
Should I include salary expectations on my resume?
No—omit salary figures. Use market research and interview conversations to negotiate compensation.
In conclusion, security resumes should prove impact and accountability
Treat the resume like an incident briefing: concise facts, the tools used, and measurable outcomes. Prioritize metric-first bullets that show detection coverage, response speed, and risk reduction. Mirror keywords from the job posting (SIEM/EDR names, MITRE, SOC 2, MTTD/MTTR) and back them up with short, verifiable accomplishments.