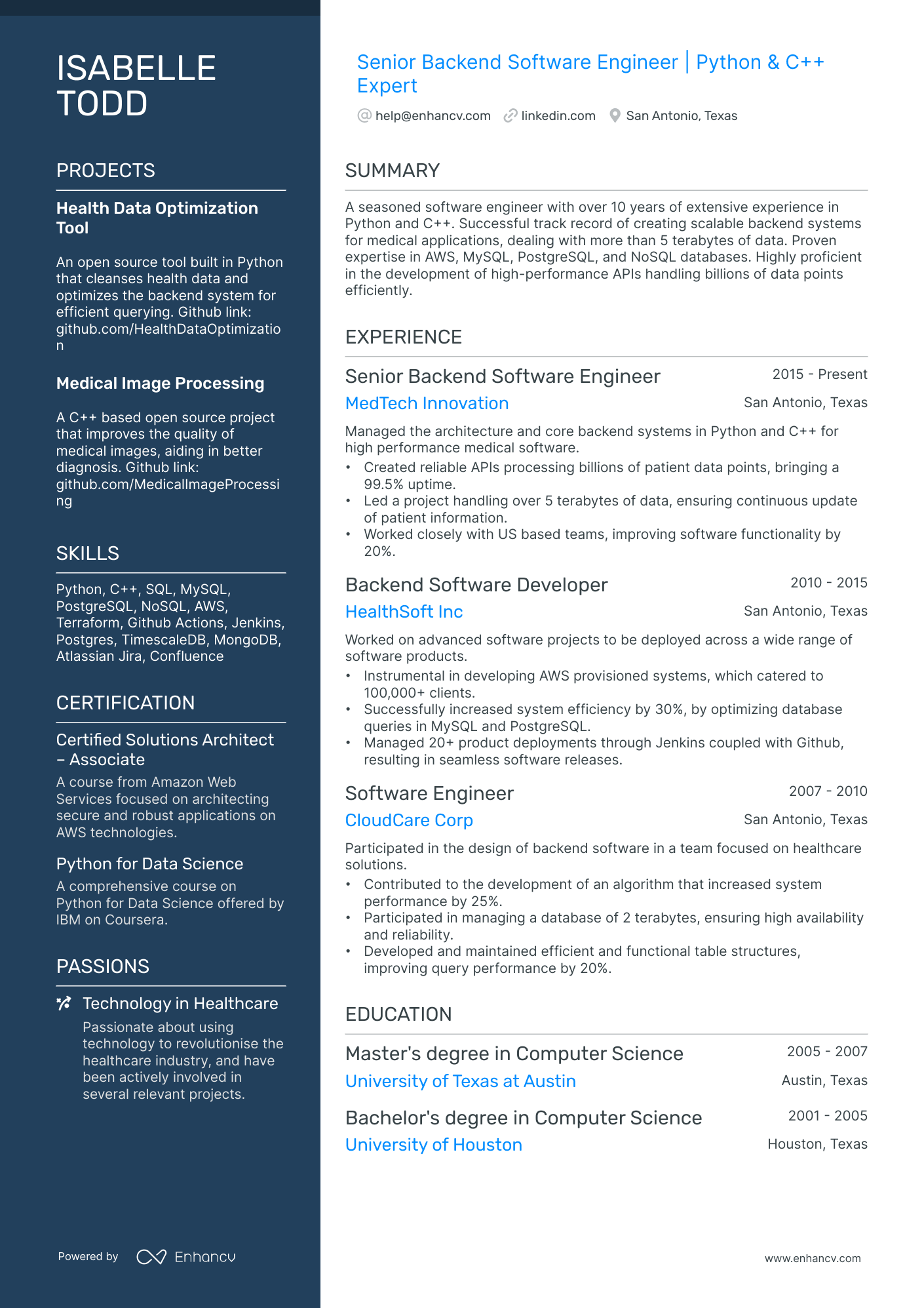
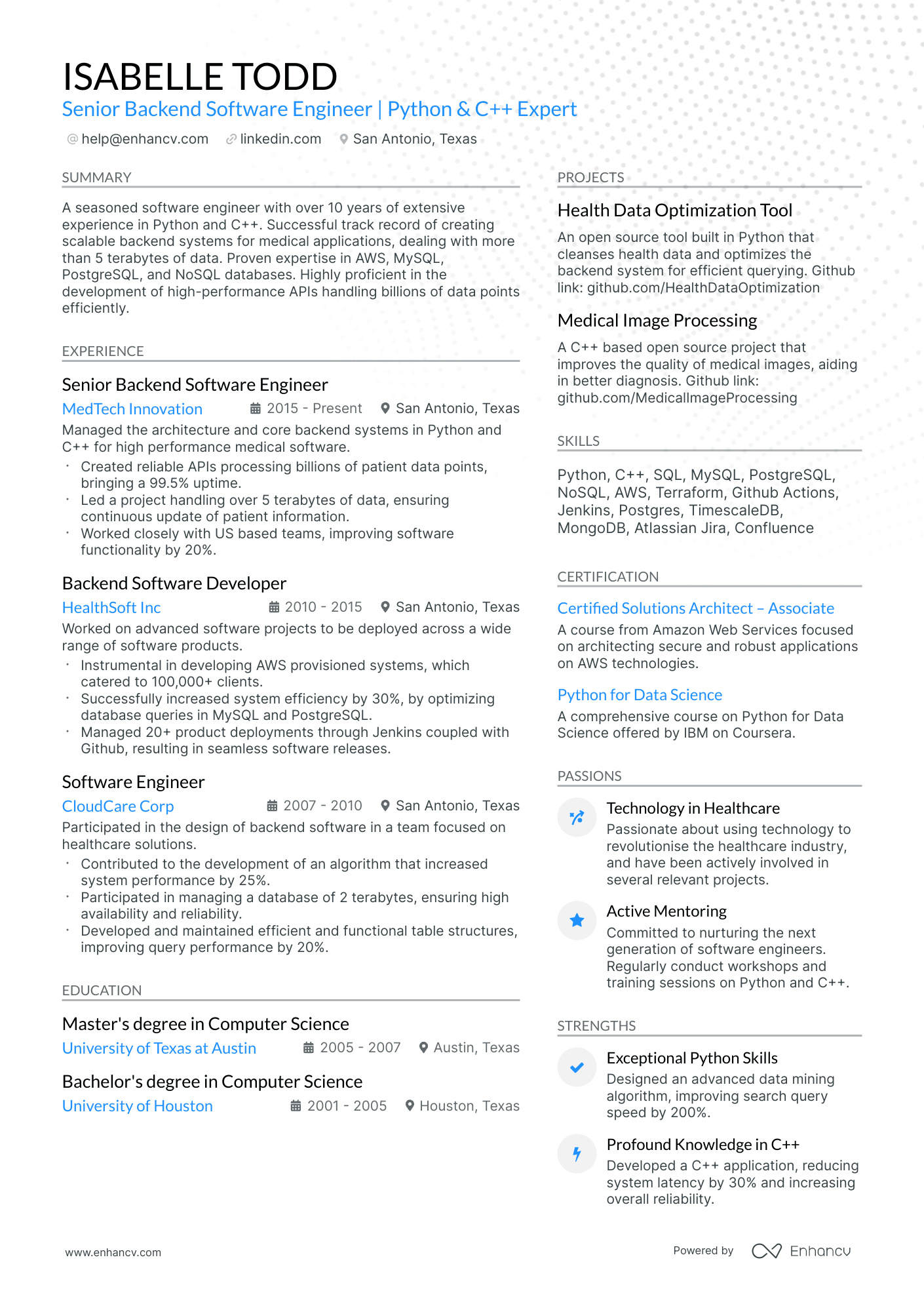
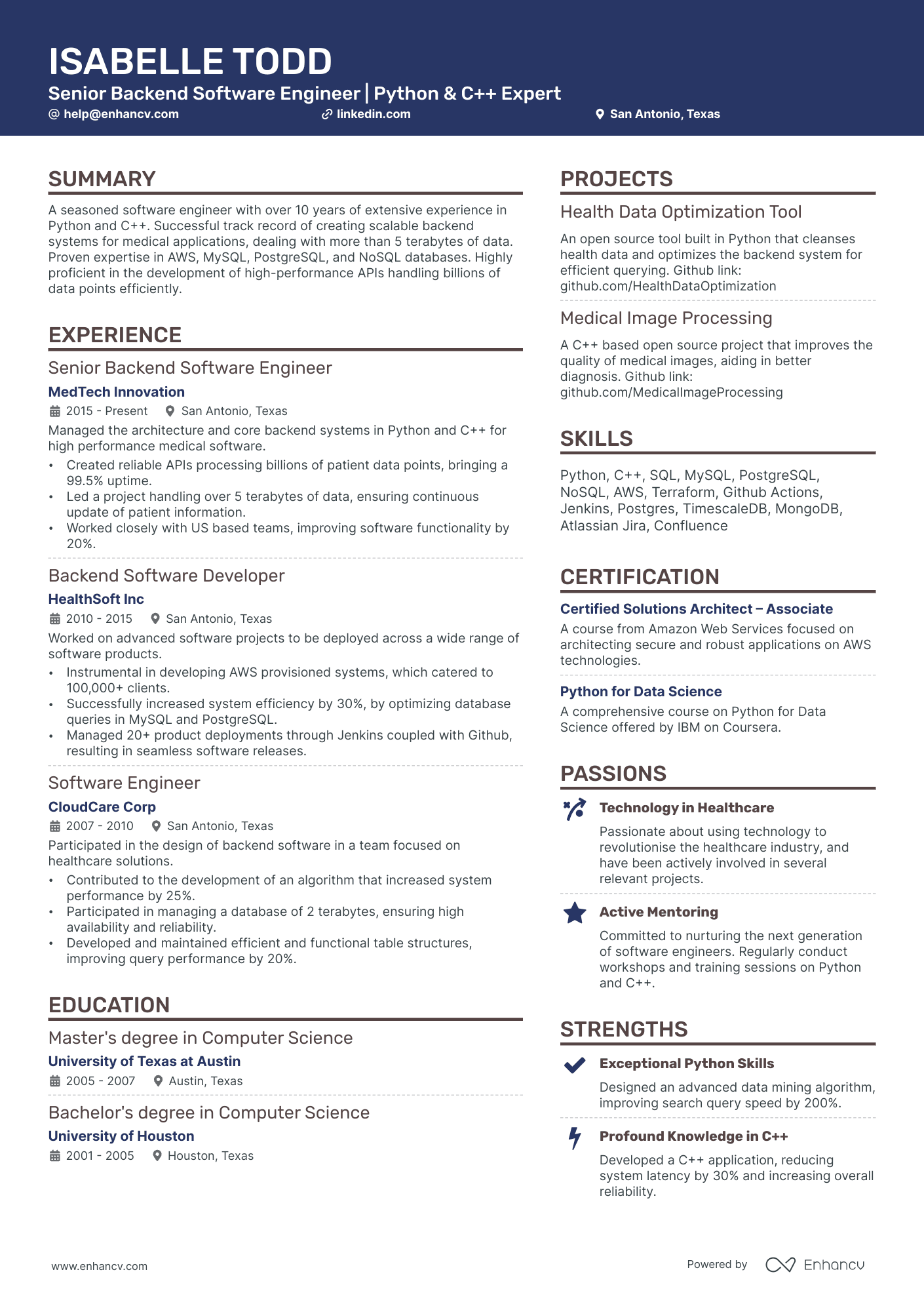
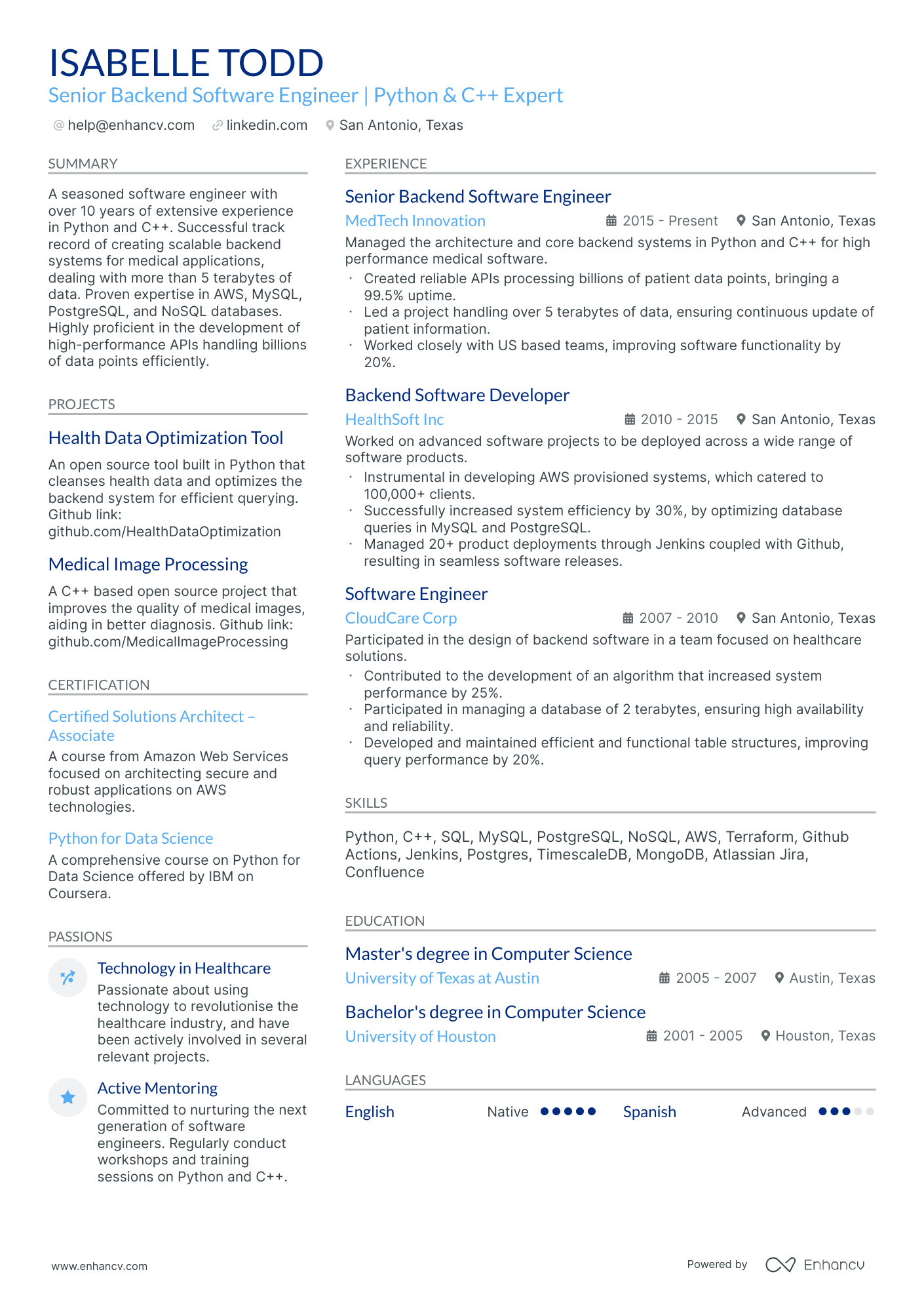
Many Cybersecurity engineer resume drafts fail because they read like tool inventories and generic duties, so they never prove risk reduction. That matters when an ATS (applicant tracking system) filters fast and recruiters scan in seconds in a crowded market.
A strong resume shows what you changed and why it mattered, not just what you used. Understanding how to write a resume that communicates impact is essential—you should quantify incidents reduced, mean time to detect improved, critical assets covered, audit findings closed, and secure releases delivered without downtime.
Key takeaways
- Quantify security outcomes like incidents reduced and response times improved on every resume.
- Tailor experience bullets to match each job posting's tools, frameworks, and terminology.
- Use reverse-chronological format for senior roles and hybrid format for career switchers.
- Prove skills through measurable results in your experience section, not just a skills list.
- Place certifications above education when they're recent and directly relevant to the role.
- Build project entries with clear scope, tools used, and results even without full-time experience.
- Use Enhancv to turn vague job duties into focused, metric-driven resume bullets faster.
Job market snapshot for Cybersecurity engineers
We analyzed 270 recent Cybersecurity engineer job ads across major US job boards. These numbers help you understand employer expectations, industry demand, experience requirements at a glance.
What level of experience employers are looking for Cybersecurity engineers
| Years of Experience | Percentage found in job ads |
|---|---|
| 1–2 years | 5.6% (15) |
| 3–4 years | 17.8% (48) |
| 5–6 years | 17.4% (47) |
| 7–8 years | 10.0% (27) |
| 9–10 years | 5.6% (15) |
| 10+ years | 6.7% (18) |
| Not specified | 41.9% (113) |
Cybersecurity engineer ads by area of specialization (industry)
| Industry (Area) | Percentage found in job ads |
|---|---|
| Finance & Banking | 61.9% (167) |
| Healthcare | 15.6% (42) |
| Education | 10.0% (27) |
| Manufacturing | 6.7% (18) |
Top companies hiring Cybersecurity engineers
| Company | Percentage found in job ads |
|---|---|
| Booz Allen Hamilton Inc. | 8.1% (22) |
| Truist Financial Corporation | 8.1% (22) |
| Cadence Bank | 7.0% (19) |
| The MITRE Corporation | 6.3% (17) |
Role overview stats
These tables show the most common responsibilities and employment types for Cybersecurity engineer roles. Use them to align your resume with what employers expect and to understand how the role is structured across the market.
Day-to-day activities and top responsibilities for a Cybersecurity engineer
| Responsibility | Percentage found in job ads |
|---|---|
| Cybersecurity | 35.9% (97) |
| Python | 33.7% (91) |
| Linux | 28.1% (76) |
| Windows | 23.3% (63) |
| Firewalls | 22.2% (60) |
| Aws | 21.9% (59) |
| Azure | 17.0% (46) |
| Network security | 14.8% (40) |
| Cissp | 14.1% (38) |
| Java | 14.1% (38) |
| Javascript | 14.1% (38) |
| Terraform | 14.1% (38) |
Type of employment (remote vs on-site vs hybrid)
| Employment type | Percentage found in job ads |
|---|---|
| On-site | 60.0% (162) |
| Hybrid | 34.4% (93) |
| Remote | 5.6% (15) |
How to format a Cybersecurity engineer resume
Recruiters evaluating cybersecurity engineers prioritize hands-on technical depth, familiarity with specific security frameworks and tooling, and evidence of protecting infrastructure at scale. Your resume format determines how quickly a hiring manager can identify these signals, so choosing the right structure directly affects whether your application advances past initial screening.
I have significant experience in this role—which format should I use?
Use a reverse-chronological format to showcase your progression through increasingly complex security environments and responsibilities. Do:
- Lead each role entry with scope and ownership—network size, team oversight, compliance frameworks managed, and security domains covered (cloud, application, endpoint, identity).
- Highlight role-specific tools and skills such as SIEM platforms (Splunk, Sentinel), IDS/IPS, vulnerability scanners (Nessus, Qualys), scripting languages (Python, Bash), and frameworks like NIST, ISO 27001, or MITRE ATT&CK.
- Quantify outcomes tied to business impact, including incident response time reductions, vulnerability remediation rates, cost savings from automation, or compliance audit results.
I'm junior or switching into this role—what format works best?
A hybrid format works best because it lets you lead with relevant security skills and certifications while still showing a clear work or project timeline. Do:
- Place a dedicated skills section near the top of the resume featuring security tools, certifications (CompTIA Security+, CEH, GSEC), and core domains like network security, threat analysis, or vulnerability management.
- Include hands-on projects, labs, CTF competitions, or transitional experience such as IT support or systems administration roles where you performed security-adjacent tasks.
- Connect every action to a measurable or observable result so hiring managers can see practical application, not just coursework.
Why not use a functional resume?
A functional format strips away the timeline context that hiring managers need to verify where and when you applied your cybersecurity skills, making it harder to assess real-world experience and easier for applicant tracking systems to misparse your qualifications. A functional format may be acceptable if you're transitioning from a non-security field (such as systems administration or software development), have significant resume gaps, or lack formal cybersecurity job titles—but only if every listed skill is tied directly to a specific project, lab, or measurable outcome rather than presented in isolation.
With your resume's structure and layout established, the next step is filling it with the right sections to showcase your cybersecurity expertise effectively.
What sections should go on a Cybersecurity engineer resume
Recruiters expect to quickly find evidence that you can secure systems, detect threats, and reduce risk in real environments. Knowing which resume sections to include ensures nothing critical gets overlooked. Use this structure for maximum clarity:
- Header
- Summary
- Experience
- Skills
- Projects
- Education
- Certifications
- Optional sections: Awards, Open-source work, Volunteering
Your strongest experience bullets should emphasize measurable impact, incident or risk scope, security outcomes, and the results you delivered.
Is your resume good enough?
Drop your resume here or choose a file. PDF & DOCX only. Max 2MB file size.
Once you’ve organized your resume with the right categories, the next step is writing your cybersecurity engineer experience section so it clearly supports each part.
How to write your Cybersecurity engineer resume experience
Your work experience section should showcase security solutions you've designed, deployed, or hardened—using role-relevant tools, frameworks, and methodologies—and the measurable outcomes those efforts produced. Hiring managers prioritize demonstrated impact on an organization's security posture over descriptive task lists that simply catalog daily responsibilities.
Each entry should include:
- Job title
- Company and location (or remote)
- Dates of employment (month and year)
Three to five concise bullet points showing what you owned, how you executed, and what outcomes you delivered:
- Ownership scope: the security infrastructure, network environments, cloud platforms, detection systems, or incident response programs you were directly accountable for as a cybersecurity engineer.
- Execution approach: the tools, frameworks, and methodologies you relied on—such as SIEM platforms, intrusion detection systems, penetration testing techniques, zero-trust architectures, or compliance standards—to assess risk and deliver secure solutions.
- Value improved: the specific dimensions of security posture you strengthened, whether that involved reducing vulnerability exposure, improving threat detection speed, increasing system uptime, tightening access controls, or lowering organizational risk.
- Collaboration context: how you partnered with DevOps teams, IT operations, compliance officers, executive leadership, or external auditors to align security initiatives with broader business and regulatory requirements.
- Impact delivered: the tangible results your work produced, expressed through improvements in risk reduction, incident response effectiveness, audit readiness, or overall resilience rather than a summary of tasks performed.
Experience bullet formula
A Cybersecurity engineer experience example
✅ Right example - modern, quantified, specific.
Cybersecurity Engineer
FinLine Payments | Remote
2022–Present
Cloud-native payments platform processing $8B+ annually across North America with a regulated, high-availability environment.
- Hardened Amazon Web Services (AWS) footprint using Terraform, AWS Organizations, and Service Control Policies, reducing critical misconfigurations by 62% and cutting mean time to remediate from six days to two days.
- Implemented detection engineering in Splunk and CrowdStrike Falcon—mapped to MITRE ATT&CK—and increased high-fidelity alert precision by 38% while lowering false positives by 27% in partnership with the security operations center (SOC).
- Led incident response for a compromised OAuth token event, coordinating engineering, product, and legal; contained within forty-five minutes, eliminated lateral movement, and prevented an estimated $450K in fraud exposure.
- Built continuous vulnerability management with Tenable, Snyk, and Jira automation, driving 91% patch compliance within fourteen days and reducing externally exposed critical findings from twenty-two to four.
- Integrated security into continuous integration and continuous delivery pipelines with GitHub Actions, Open Policy Agent (OPA), and secret scanning, blocking 100% of detected credential leaks pre-merge and saving an estimated 120 engineering hours per quarter.
Now that you've seen what a strong experience section looks like in practice, let's break down how to adapt yours to match the specific job you're targeting.
How to tailor your Cybersecurity engineer resume experience
Recruiters evaluate your cybersecurity engineer resume through both human review and applicant tracking systems (ATS). Tailoring your resume to the job description ensures you pass both filters.
Ways to tailor your Cybersecurity engineer experience:
- Match specific SIEM platforms and EDR tools named in the posting.
- Mirror the exact compliance frameworks listed like NIST or ISO 27001.
- Use the same terminology for incident response phases and procedures.
- Highlight vulnerability assessment methods referenced in the job description.
- Include relevant industry experience such as finance or healthcare security.
- Emphasize zero trust architecture work if the role references it.
- Reflect the collaboration models mentioned like SOC team integration.
- Align your threat detection metrics with the KPIs they prioritize.
Tailoring means aligning your real accomplishments with what the role demands, not forcing keywords where they don't belong.
Resume tailoring examples for Cybersecurity engineer
| Job description excerpt | Untailored | Tailored |
|---|---|---|
| "Perform vulnerability assessments and penetration testing using Nessus and Burp Suite across cloud and on-premises environments" | Conducted security assessments and identified vulnerabilities across company systems. | Executed quarterly vulnerability assessments and penetration tests using Nessus and Burp Suite across 200+ AWS and on-premises assets, remediating 94% of critical findings within SLA. |
| "Develop and maintain SIEM detection rules in Splunk to identify advanced persistent threats and reduce mean time to detect (MTTD)" | Monitored security alerts and helped improve incident detection processes. | Authored and tuned 60+ Splunk SIEM correlation rules targeting advanced persistent threat tactics mapped to MITRE ATT&CK, reducing MTTD from 48 hours to 12 hours. |
| "Lead incident response efforts, conduct forensic analysis, and produce post-incident reports aligned with NIST 800-61 framework" | Responded to security incidents and created reports for management review. | Led incident response for 30+ security events annually, performed disk and memory forensic analysis using EnCase and Volatility, and delivered post-incident reports aligned with NIST 800-61 that drove 15 process improvements. |
Once your experience aligns with the role’s priorities, the next step is to quantify your cybersecurity engineer achievements so hiring teams can quickly see your impact.
How to quantify your Cybersecurity engineer achievements
Quantifying your achievements shows how you reduced risk, improved detection, and sped up response. Focus on incident response time, vulnerability reduction, control coverage, false positives, and cost savings from automation.
Quantifying examples for Cybersecurity engineer
| Metric | Example |
|---|---|
| Incident response time | "Cut mean time to respond from 2 hours to 35 minutes by tuning Splunk alerts and automating triage with SOAR playbooks." |
| Vulnerability reduction | "Reduced critical vulnerabilities by 62% in ninety days by prioritizing CVSS 9+ findings and enforcing patch service level agreements across 180 servers." |
| Detection quality | "Lowered false-positive rate by 41% by refining Sigma rules and endpoint detections in Microsoft Defender for Endpoint across 2,400 endpoints." |
| Control coverage | "Raised multi-factor authentication coverage from 78% to 99% by enforcing conditional access policies for all privileged accounts in Azure Active Directory." |
| Cost efficiency | "Saved $120,000 annually by consolidating endpoint security agents and retiring three redundant tools after a ninety-day proof of concept." |
Turn vague job duties into measurable, recruiter-ready resume bullets in seconds with Enhancv's Bullet Point Generator.
Once your bullet points clearly convey your impact, the next step is ensuring your skills section reinforces that expertise with the right mix of technical and interpersonal abilities.
How to list your hard and soft skills on a Cybersecurity engineer resume
Your skills section shows you can prevent, detect, and respond to threats; recruiters and applicant tracking systems (ATS) scan this section for role-specific keywords and tool matches, so aim for a balanced mix of hard skills and execution-focused soft skills. Cybersecurity engineer roles require a blend of:
- Product strategy and discovery skills.
- Data, analytics, and experimentation skills.
- Delivery, execution, and go-to-market discipline.
- Soft skills.
Your skills section should be:
- Scannable (bullet-style grouping).
- Relevant to the job post.
- Backed by proof in experience bullets.
- Updated with current tools.
Place your skills section:
- Above experience if you're junior or switching careers.
- Below experience if you're mid/senior with strong achievements.
Hard skills
- Threat modeling, STRIDE
- Network security, TCP/IP, DNS
- SIEM: Splunk, Microsoft Sentinel
- EDR: CrowdStrike Falcon, Microsoft Defender for Endpoint
- Vulnerability management: Tenable, Qualys
- Incident response, NIST 800-61
- Detection engineering, Sigma rules
- Log analysis, KQL, SPL
- Cloud security: AWS, Azure, IAM
- Infrastructure as Code: Terraform
- Container security: Kubernetes, Docker
- Security hardening, CIS Benchmarks
Soft skills
- Write clear incident reports
- Triage alerts under pressure
- Prioritize risk by impact
- Communicate tradeoffs to leadership
- Partner with IT and DevOps
- Lead incident response calls
- Drive remediation to closure
- Challenge assumptions with evidence
- Document runbooks and standards
- Coordinate across time zones
- Mentor analysts on detections
- Present findings to stakeholders
How to show your Cybersecurity engineer skills in context
Skills shouldn't live only in a bulleted list on your resume. Explore how other professionals present their resume skills effectively to see what works in practice.
They should be demonstrated in:
- Your summary (high-level professional identity)
- Your experience (proof through outcomes)
Here's what strong, skill-rich entries look like in practice.
Summary example
Senior cybersecurity engineer with 10 years securing cloud-native environments across fintech. Skilled in SIEM tuning, zero-trust architecture, and threat modeling. Led incident response improvements that cut mean detection time by 62%. Known for cross-team collaboration under pressure.
- Signals senior-level depth immediately
- Names specific tools and frameworks
- Leads with a measurable outcome
- Highlights collaboration as a strength
Experience example
Senior Cybersecurity Engineer
Vantage Security Group | Remote
March 2020–Present
- Deployed CrowdStrike Falcon and custom SIEM correlation rules, reducing false positive alerts by 74% and freeing analysts for higher-priority investigations.
- Partnered with DevOps to integrate SAST/DAST scanning into CI/CD pipelines, cutting production vulnerabilities by 53% within six months.
- Led quarterly red team exercises with a five-person security team, identifying and remediating 38 critical misconfigurations across AWS infrastructure.
- Every bullet includes measurable proof
- Skills appear naturally within achievements
Once you’ve demonstrated your cybersecurity engineering skills through concrete examples and results, the next step is learning how to build a cybersecurity engineer resume with no experience that uses those same proof points effectively.
How do I write a Cybersecurity engineer resume with no experience
Even without full-time experience, you can demonstrate readiness through projects and self-directed learning. Building a resume without work experience is entirely possible when you focus on evidence-backed proof points:
- Home lab with SIEM alerts
- Capture the flag competition write-ups
- Open-source security tool contributions
- Bug bounty findings and reports
- Security coursework capstone project
- Internship, volunteer, or campus IT
- Incident response tabletop exercises
- Threat hunting case studies portfolio
Focus on:
- Evidence-backed projects with metrics
- Security tools used in context
- Clear scope, method, and results
- Relevant certifications and labs
Resume format tip for entry-level Cybersecurity engineer
Use a skills-based resume format because it puts projects, labs, and tools above work history while you build experience. Do:
- Put a "Projects" section first.
- List tools per project, not only.
- Quantify results: alerts, hosts, time.
- Include links to reports and code.
- Match keywords to the job post.
- Built a home lab SIEM using Splunk, Sysmon, and Sigma rules; reduced false positives by 30% after tuning five detections across three Windows hosts.
Your education section plays a key role in compensating for limited work experience, so presenting it effectively is essential.
How to list your education on a Cybersecurity engineer resume
Your education section helps hiring teams confirm you have the foundational knowledge a cybersecurity engineer needs. It validates your technical training and academic background quickly.
Include:
- Degree name
- Institution
- Location
- Graduation year
- Relevant coursework (for juniors or entry-level candidates)
- Honors & GPA (if 3.5 or higher)
Skip month and day details—list the graduation year only.
Here's a strong education entry tailored for a cybersecurity engineer resume:
Example education entry
Bachelor of Science in Computer Science
Georgia Institute of Technology, Atlanta, GA
Graduated 2021
GPA: 3.7/4.0
- Relevant Coursework: Network Security, Cryptography, Ethical Hacking, Operating Systems, Digital Forensics
- Honors: Dean's List (six semesters), Magna Cum Laude
How to list your certifications on a Cybersecurity engineer resume
Certifications on your resume show a Cybersecurity engineer's commitment to continuous learning, hands-on tool proficiency, and current industry knowledge. They also help recruiters quickly confirm role-specific skills and security standards familiarity.
Include:
- Certificate name
- Issuing organization
- Year
- Optional: credential ID or URL
- Place certifications below education when your degree is recent and your certifications are older or less relevant to the Cybersecurity engineer role.
- Place certifications above education when they are recent, highly relevant, or required for the Cybersecurity engineer role you target.
Best certifications for your Cybersecurity engineer resume
- CompTIA Security+
- CompTIA CySA+
- Certified Information Systems Security Professional (CISSP)
- Certified Ethical Hacker (CEH)
- GIAC Security Essentials (GSEC)
- GIAC Certified Incident Handler (GCIH)
- AWS Certified Security—Specialty
Once you’ve positioned your certifications where they’re easy to verify and aligned with the role, you’re ready to write your cybersecurity engineer resume summary to reinforce those qualifications upfront.
How to write your Cybersecurity engineer resume summary
Your resume summary is the first thing a recruiter reads, so it needs to earn their attention fast. A strong summary positions you as a capable cybersecurity engineer who solves real problems.
Keep it to three to four lines, with:
- Your title and total years of cybersecurity engineering experience.
- The domain you work in, such as cloud security, enterprise networks, or financial services.
- Core tools and technologies like SIEM platforms, firewalls, IDS/IPS, or penetration testing frameworks.
- One or two measurable achievements, such as reduced incidents or improved response times.
- Soft skills tied to outcomes, like cross-team collaboration that streamlined incident workflows.
PRO TIP
At the mid-level, focus on technical depth, hands-on tool expertise, and measurable security improvements. Highlight specific projects where your work reduced risk or strengthened defenses. Avoid vague descriptors like "passionate" or "motivated self-starter." Skip objective statements that center on what you want rather than what you deliver.
Example summary for a Cybersecurity engineer
Cybersecurity engineer with four years of experience securing cloud and enterprise environments. Deployed SIEM and IDS/IPS solutions that cut mean incident response time by 35%. Skilled in vulnerability assessment, Python scripting, and cross-functional threat remediation.
Optimize your resume summary and objective for ATS
Drop your resume here or choose a file.
PDF & DOCX only. Max 2MB file size.
Now that your summary captures your cybersecurity expertise at a glance, make sure your header gives recruiters the essential contact and professional details they need to actually reach you.
What to include in a Cybersecurity engineer resume header
A resume header lists your key contact details and professional links, helping a Cybersecurity engineer stand out in searches and pass recruiter screening fast.
Essential resume header elements
- Full name
- Tailored job title and headline
- Location
- Phone number
- Professional email
- GitHub link
- Portfolio link
A LinkedIn link helps recruiters confirm your roles, dates, and endorsements quickly, which supports faster screening.
Don't include a photo on a Cybersecurity engineer resume unless the role is explicitly front-facing or appearance-dependent.
Keep the header to one to two lines, mirror the job title, and use links that open to your strongest, most relevant work.
Cybersecurity engineer resume header
Jordan Lee
Cybersecurity engineer | Incident response and cloud security
Austin, TX
(512) 555-01XX
jordan.lee@enhancv.com
github.com/jordanlee yourwebsite.com linkedin.com/in/jordanlee
Once your contact details and key identifiers are set at the top, add targeted additional sections to round out your cybersecurity engineer resume and reinforce your fit.
Additional sections for Cybersecurity engineer resumes
Adding extra sections strengthens your resume when they highlight specialized expertise or credibility that core sections can't fully capture.
- Certifications (CISSP, CEH, CompTIA Security+, OSCP)
- Publications and research
- Security conferences and speaking engagements
- Bug bounty achievements
- Professional affiliations (ISSA, ISACA, (ISC)²)
- Languages
- Open-source security contributions
Once your resume's additional sections round out your professional profile, pairing it with a tailored cover letter can strengthen your application even further.
Do Cybersecurity engineer resumes need a cover letter
A cover letter isn't required for a Cybersecurity engineer, but it helps in competitive roles or teams with strict hiring expectations. If you're unsure what a cover letter is or when to use one, it can make a difference when your resume needs context, or when you want to show clear fit.
Use a cover letter to add details your resume can't:
- Explain role and team fit: Match your experience to the job's security goals, tooling, and operating model.
- Highlight one or two relevant projects or outcomes: Name the system, your actions, and the measurable result, such as reduced risk or faster detection.
- Show understanding of the product, users, or business context: Connect security work to customer impact, compliance needs, or uptime requirements.
- Address career transitions or non-obvious experience: Translate adjacent work into security value, and clarify any title changes, gaps, or domain shifts.
Drop your resume here or choose a file.
PDF & DOCX only. Max 2MB file size.
Once you’ve decided whether to include a cover letter to add context beyond your resume, the next step is using AI to strengthen your cybersecurity engineer resume so it communicates your value more clearly and efficiently.
Using AI to improve your Cybersecurity engineer resume
AI can sharpen your resume's clarity, structure, and impact. It helps refine wording and highlight results. But overuse can strip authenticity. If you're exploring which AI is best for writing resumes, start with targeted prompts and stop once your content feels clear and role-aligned.
Here are 10 practical prompts to strengthen specific sections of your Cybersecurity engineer resume:
Strengthen your summary
Quantify experience bullets
Align skills to job posts
Sharpen action verbs
Refine project descriptions
Optimize certifications placement
Tighten education details
Remove filler language
Tailor for ATS
Improve bullet structure
Conclusion
A strong Cybersecurity engineer resume ties impact to numbers and scope, such as incidents reduced, response times improved, and risks mitigated. It highlights role-specific skills, including threat detection, incident response, vulnerability management, and secure architecture.
Keep the structure clean and easy to scan, with focused sections, consistent formatting, and clear keywords. This approach shows you can deliver results now and stay effective as tools, threats, and hiring needs evolve.