Crafting a CV that showcases your diverse skill-set and experience in cyber security can be a daunting task. Our guide offers targeted advice to effectively highlight your qualifications and stand out to potential employers in the field of cyber security.
- Answer job requirements with your cyber security analyst CV and experience;
- Curate your academic background and certificates, following industry-leading CV examples;
- Select from +10 niche skills to match the ideal candidate profile
- Write a more succinct experience section that consists of all the right details.
Do you need more specific insights into writing your cyber security analyst CV? Our guides focus on unique insights for each individual role:
CV examples for cyber security analyst
By Experience
Senior Cyber Security Analyst
- Structured layout enhances readability - The CV is meticulously organized, with clearly defined sections such as experience, education, skills, and achievements, which allow the reader to easily navigate through the candidate's background and qualifications. Each bullet point in the experience section conveys a specific accomplishment concisely, illustrating the candidate's impact efficiently.
- Career progression showcases steady advancement - Daniel's career trajectory highlights a progression from IT Security Specialist to Senior Cyber Security Analyst, reflecting a solid upward movement within the cybersecurity industry. Each role adds new responsibilities and expertise, such as transitioning from technical tasks to leadership roles coordinating cross-functional teams.
- Technical expertise with industry-specific tools - The CV includes an impressive array of cybersecurity tools and methodologies like SIEM systems, MFA, and Kusto Query Language (KQL), indicating a deep understanding of the field and technical proficiency. This specialization aligns with the demands of a Senior Cyber Security Analyst role, showcasing Daniel's capacity to handle sophisticated security operations.
Junior Cyber Security Analyst
- Structured presentation enhances readability - The CV is meticulously organized into sections that are easy to navigate, allowing quick access to crucial information. Key components such as experience, skills, education, and achievements are clearly defined, reflecting the candidate's professionalism and attention to detail.
- Progression in Cyber Security expertise - Harper Webb showcases a trajectory of professional growth from an Information Security Intern to a Cyber Security Analyst, demonstrating a deepening expertise in managing and mitigating security risks. Each role builds upon the last, with enhanced responsibilities and greater contributions over time.
- Technical proficiency in industry-specific tools - The CV highlights a sophisticated understanding of cybersecurity tools and practices, including EDR solutions and Microsoft Security Technology. This technical depth underscores Harper's capability to operate in complex security environments and contribute to effective risk mitigation strategies.
Lead Cyber Security Analyst
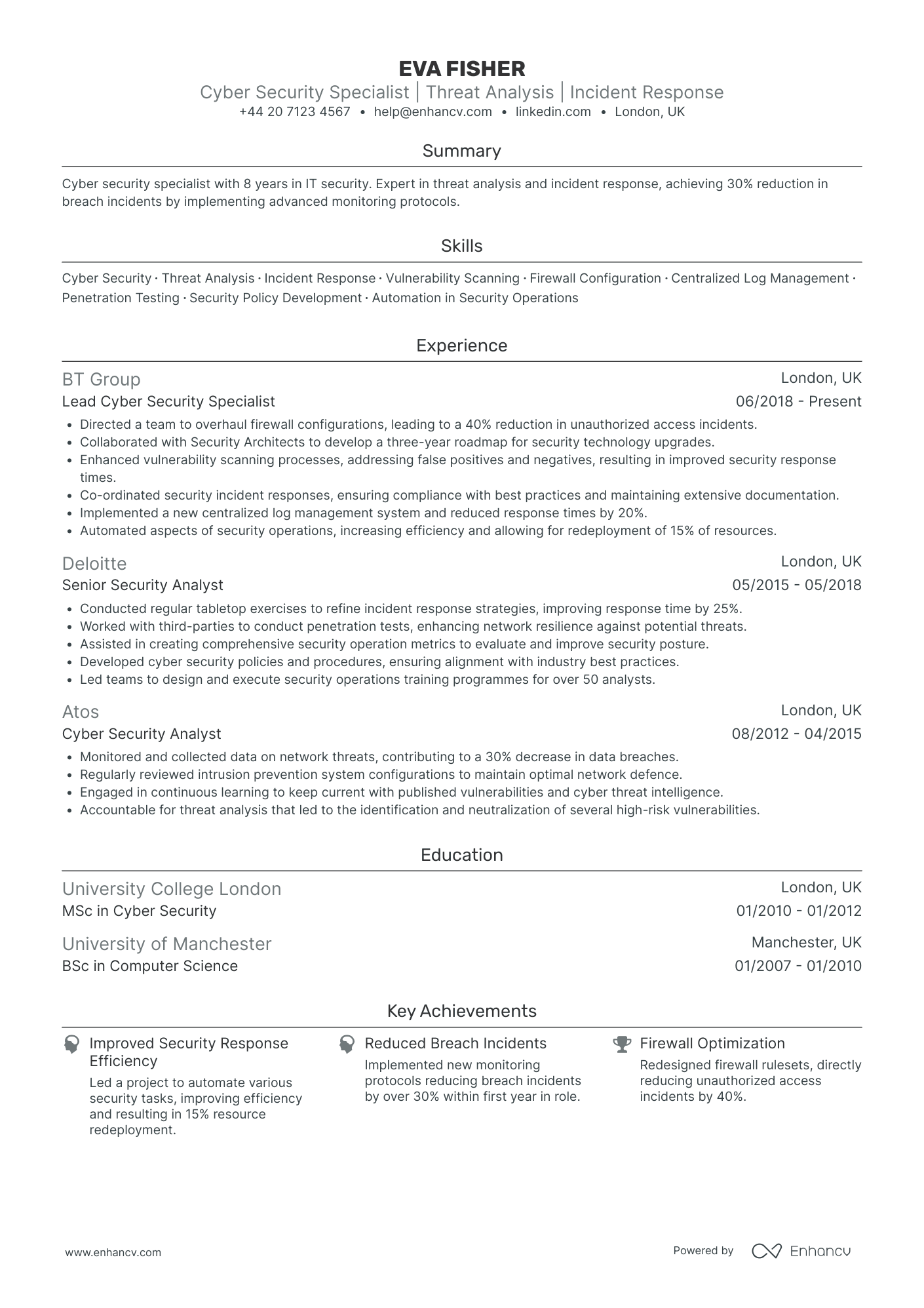
- Clear Structure and Conciseness - The CV is well-organized, ensuring each section flows logically into the next, from summary and experience to education and additional skills. The use of bullet points effectively communicates Eva Fisher's key responsibilities and achievements in a concise manner, facilitating quick comprehension by the reader.
- Impressive Career Progression - Eva Fisher shows a clear growth trajectory, moving from a Cyber Security Analyst role at Atos to a Lead Cyber Security Specialist position at BT Group within a span of six years. Her promotions indicate increasing levels of responsibility and complexity in her roles, demonstrating her capability to handle more demanding tasks over time.
- Adaptability and Cross-Functional Experience - Besides her technical prowess, Eva has collaborated with diverse teams, including Security Architects and third-party penetration testers, which highlights her ability to work cross-functionally. This indicates her adaptability to different teamwork scenarios and her capability to integrate efficiently in varied team dynamics.
Principal Cyber Security Analyst
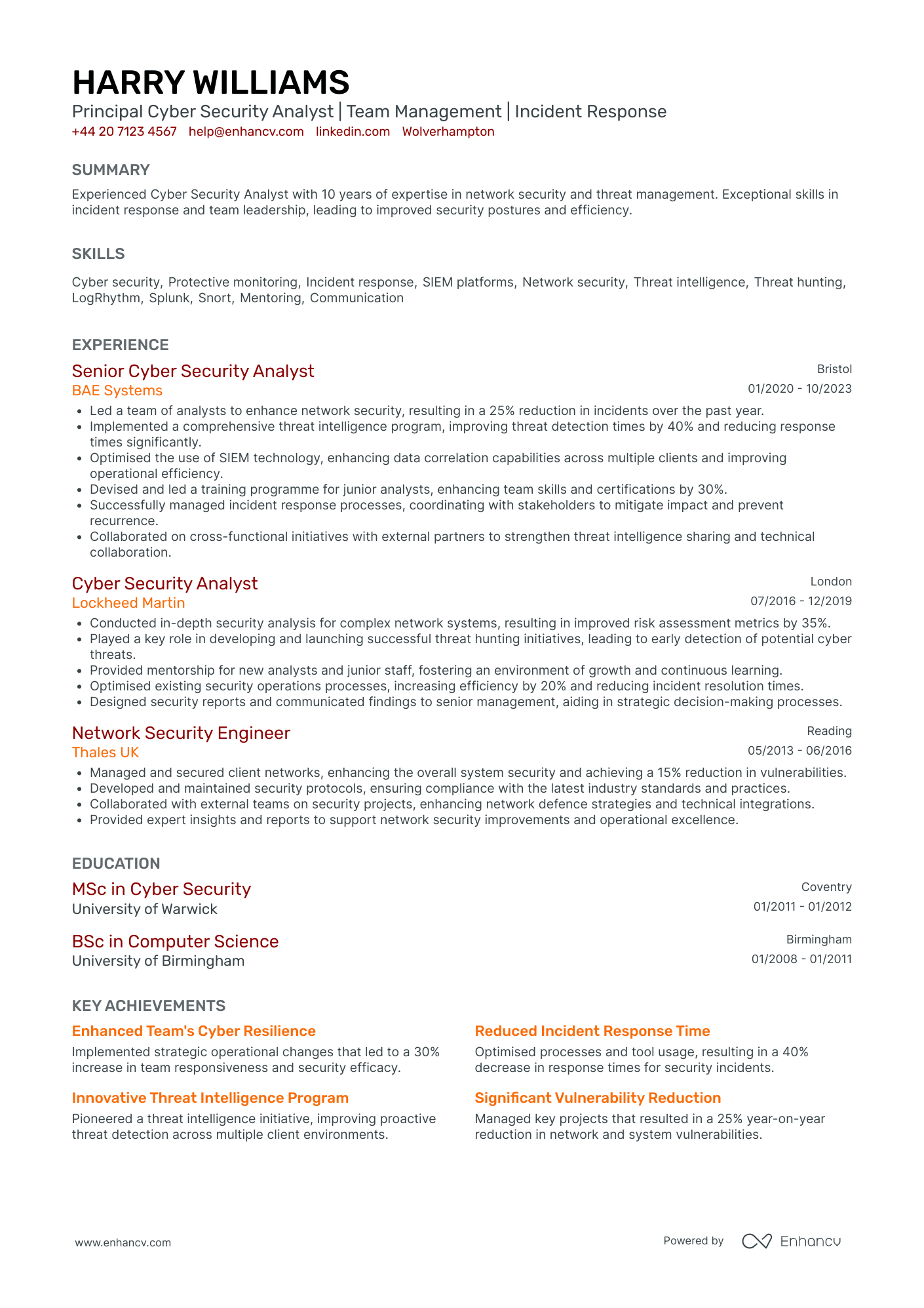
- Clear and Concise Structure - The CV is structured with clarity, presenting the candidate's information in a straightforward manner. Each section is clearly separated, making it easy to navigate through the educational background, professional experience, skills, and additional qualifications. This structure allows potential employers to quickly identify key information.
- Career Growth and Industry Relevance - The trajectory of the candidate’s career reflects consistent growth and advancement, having moved from a Network Security Engineer to a Principal Cyber Security Analyst. This progression is within prestigious companies such as BAE Systems, Lockheed Martin, and Thales UK, highlighting adaptability and industry recognition for expertise in cybersecurity.
- Emphasis on Impactful Achievements - Not just numerical outcomes, but the CV highlights achievements with direct business relevance. For instance, the reduction of incidents at BAE Systems and the development of effective threat intelligence programs emphasize the candidate’s contribution to enhancing security measures and operational efficiency, which are crucial to the roles this CV targets.
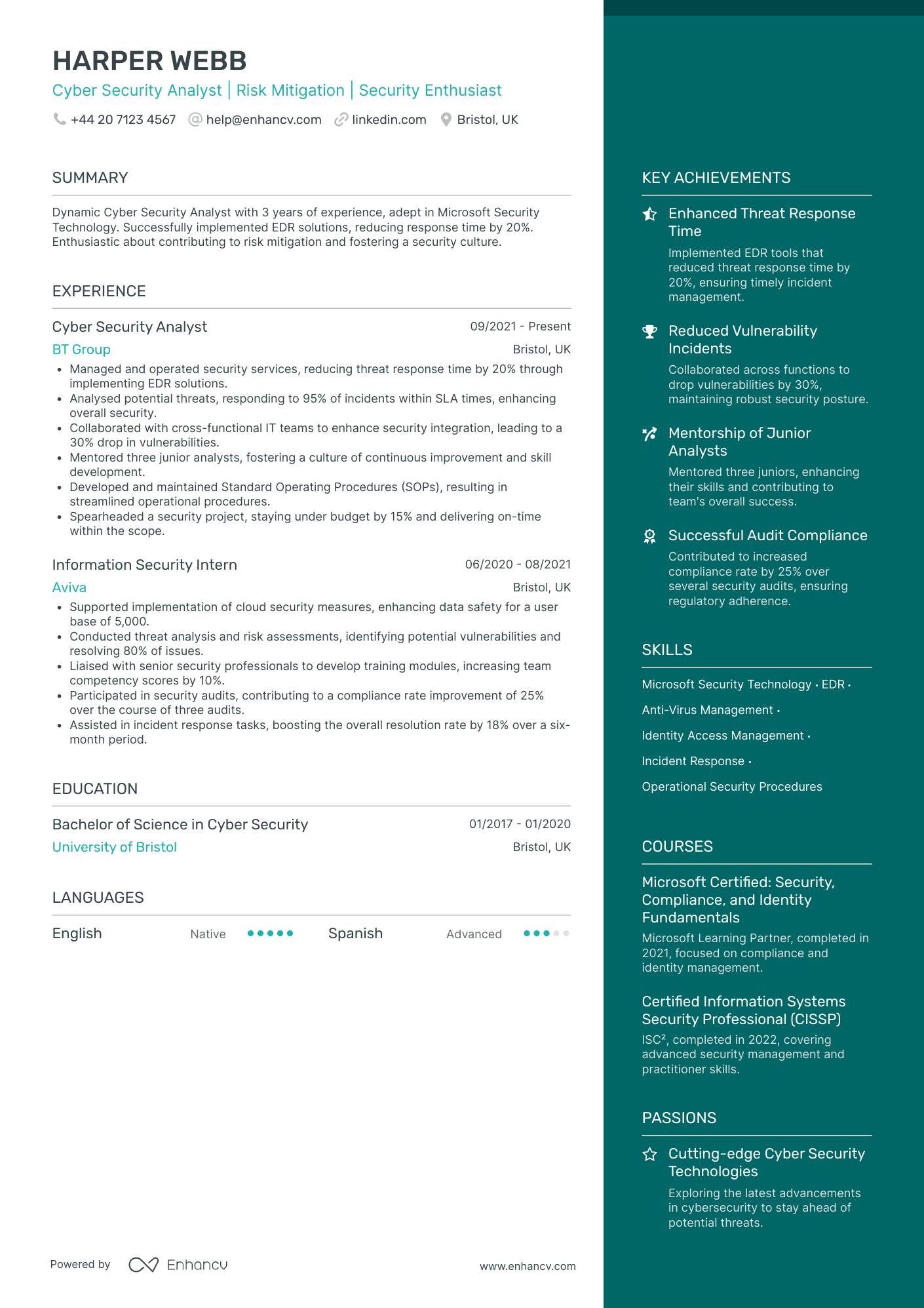
Entry-Level Cyber Security Analyst
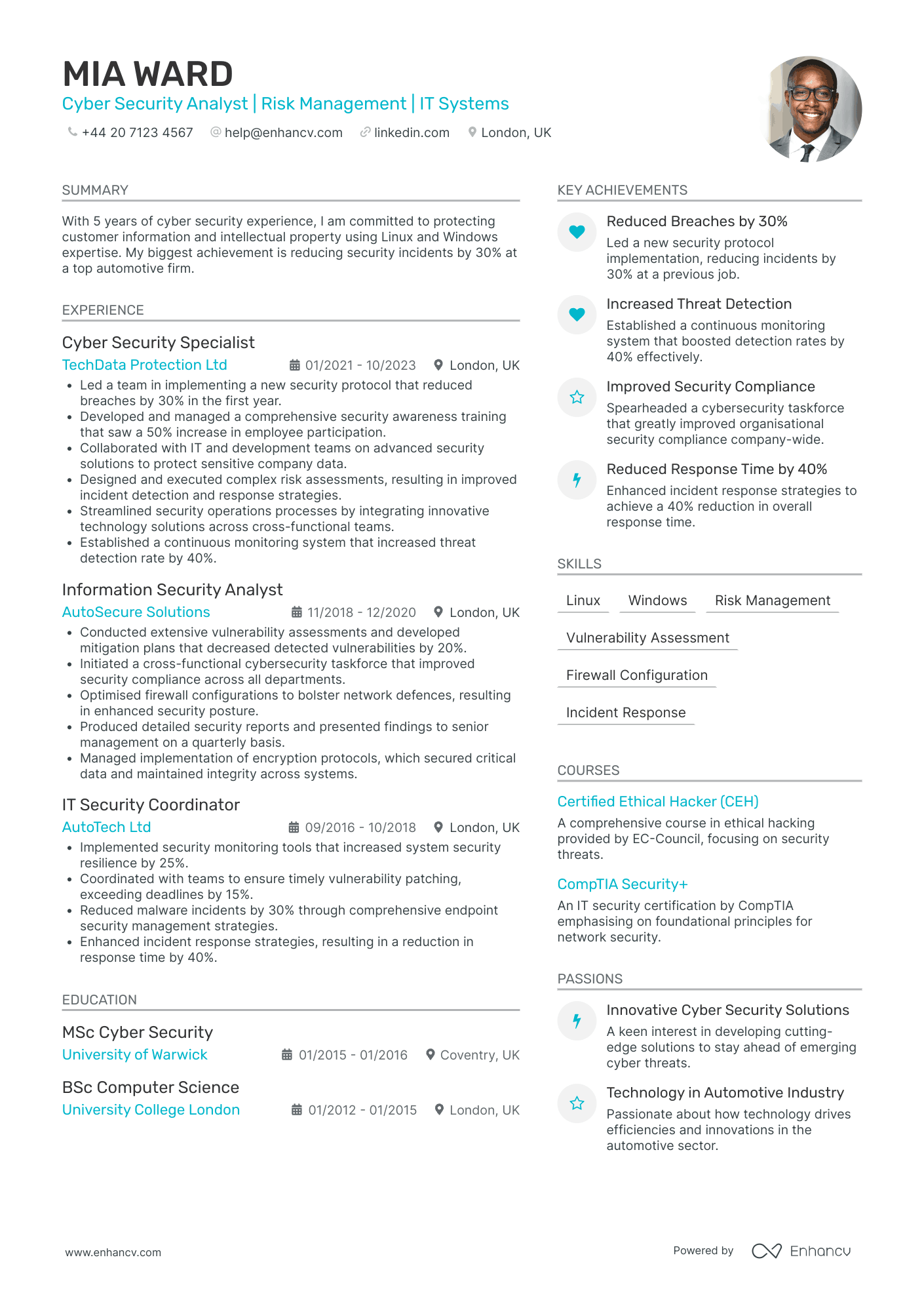
- Progressive Career Development - Mia's CV highlights a clear trajectory of growth, moving from an IT Security Coordinator to a Cyber Security Specialist. This demonstrates her ability to advance within the cybersecurity field, gaining increased responsibilities and leading key initiatives over the years. Such a career path showcases her dedication to developing her expertise and leadership capabilities in cybersecurity.
- Technical Depth and Industry Relevance - The CV stands out with its focus on industry-specific tools and methodologies, including Linux, Windows, and advanced security solutions. Mia's technical proficiency is further evidenced by her achievements in areas like encryption protocols and firewall configuration, which are crucial for protecting sensitive data within IT systems and critical infrastructure.
- Transformational Achievements with Business Impact - Mia's accomplishments are not just quantified; they are tied to significant business outcomes. For example, implementing a security protocol that reduced breaches by 30% directly benefits the organization's reputation and operational efficiency. Her work on threat detection and incident response strategies demonstrates a capacity to drive impactful change, safeguarding company assets and enhancing security posture.
Associate Cyber Security Analyst
- Comprehensive career progression - The CV illustrates a clear and impressive career trajectory, charting a steady ascent from an Information Security Officer at Rolls-Royce to a Cyber Security Analyst at BAE Systems. Each role builds upon the last, demonstrating growth in responsibility and expertise within the cyber security and risk management field.
- Industry-specific expertise and methodologies - The candidate showcases familiarity with advanced cyber security frameworks and methodologies, such as Mitre ATT&CK and NIST standards. This expertise highlights their technical depth and ability to leverage industry-recognized frameworks to enhance threat detection and risk management efforts.
- Interdisciplinary collaboration and leadership - A strong emphasis is placed on cross-functional collaboration, with the candidate actively engaging with various teams and departments to integrate behavioural and technological elements into security frameworks. Their leadership in facilitating workshops and guiding cross-departmental initiatives underscores their effectiveness in leading teams towards common security goals.
By Role
Cyber Security Risk Analyst
- Structured presentation with strategic focus - Grace Bailey’s CV is meticulously organized, providing clear and concise information that allows for easy navigation. Each section flows seamlessly into the next, ensuring that the reader quickly grasps her qualifications and accomplishments. The use of bullet points and structured dates enhances readability, reinforcing her methodical approach to cybersecurity.
- Impressive career progression with industry relevance - Grace's career trajectory showcases a steady progression within the cybersecurity field, moving up from Network Security Specialist to Information Security Analyst. Her roles at major pharmaceutical companies like Pfizer and GSK underline her strong industry footprint and experience in high-stakes environments, reflecting her capability to handle complex security challenges.
- Robust demonstration of achievements with business impact - Notably, the CV details significant achievements such as a 30% reduction in potential cyber vulnerabilities and a 40% improvement in employee security awareness, which directly impact business resilience and data security. These accomplishments highlight Grace’s ability to not only implement effective protocols but also enhance overall security posture across organizations.
Cyber Security Threat Intelligence Analyst
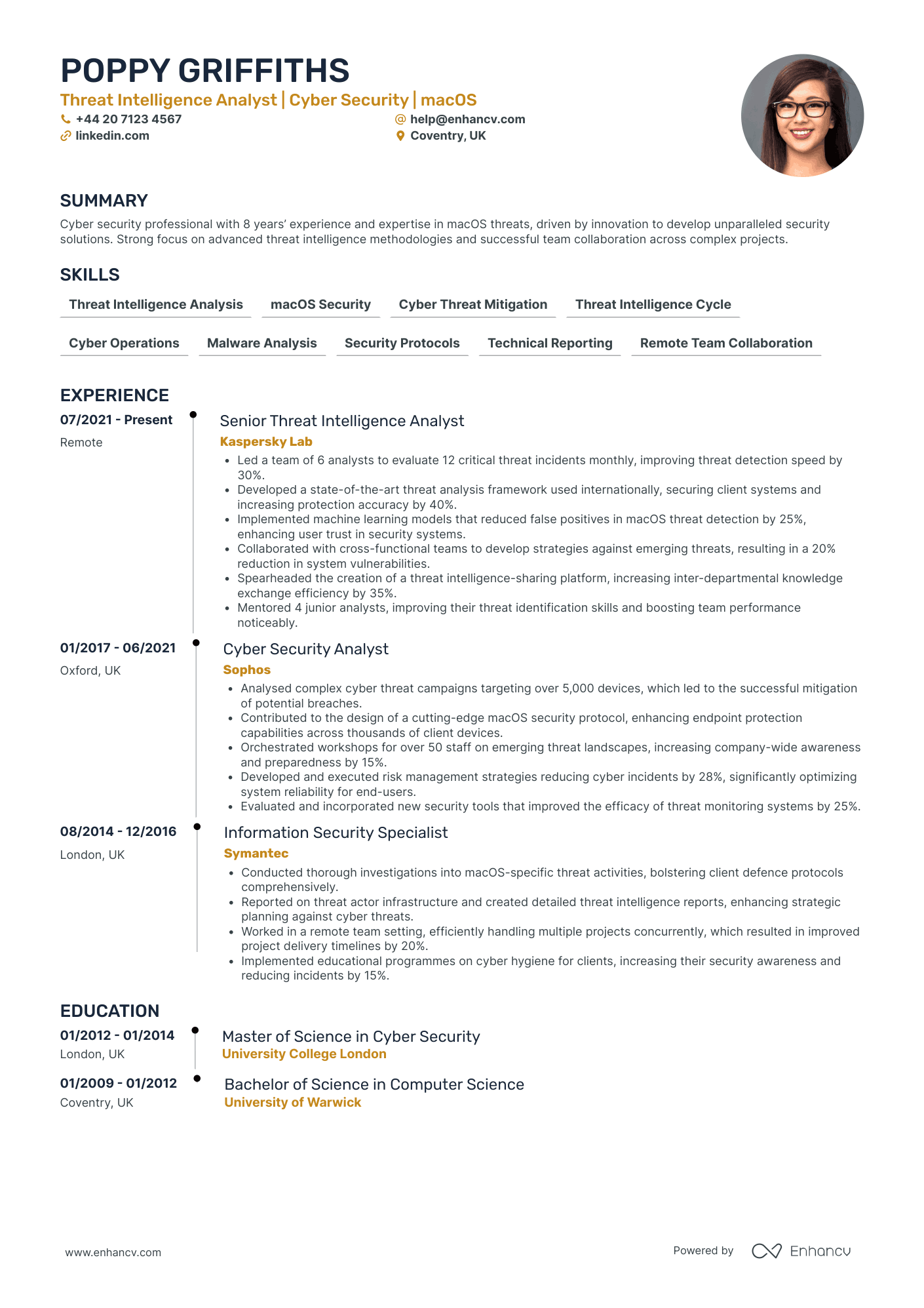
- Structured Clarity in Presentation - The CV employs a clean and logical structure, making it easy to navigate through the candidate's career history, skills, and achievements. Each section is concise yet informative, ensuring the reader can quickly comprehend Poppy Griffiths' qualifications and experience in threat intelligence and cyber security.
- Progressive Career Trajectory - Poppy Griffiths demonstrates a clear career advancement path, moving from an Information Security Specialist to a Senior Threat Intelligence Analyst. This progression showcases both growing expertise in the cyber security domain and the ability to take on more complex responsibilities and leadership roles within prominent organizations.
- Impactful Achievements with Business Relevance - The CV highlights significant achievements like reducing threat detection times and vulnerabilities, illustrating not just technical prowess but also the business value of enhancing system security and protection. These measures are directly aligned with improving client confidence and operational efficiency within the companies she has worked for.
Cyber Security Compliance Analyst
- Clear career progression and growth - The CV delineates a well-defined career trajectory, starting from a Compliance Officer at Deloitte and progressing to a Security Compliance Analyst at IBM. Each role demonstrates incremental responsibility and complexity, signifying not just industry knowledge but also a deepening expertise and impact, which is crucial for someone in a compliance-oriented role.
- Emphasis on cross-functional collaboration and leadership - Alexander's CV highlights significant experience in leading cross-functional teams, suggesting strong leadership and collaborative capabilities. The involvement in vendor compliance enhancement and incident response teams further underscores his ability to lead within diverse environments, enhancing team performance and achieving strategic goals.
- Comprehensive skill set tailored to the role - The inclusion of specific certifications like CISSP and CRISC, alongside a proficiency in GRC tools and various industry standards such as NIST CSF and PCI DSS, underscores a deep technical knowledge relevant to security compliance. This technical depth reinforces Alexander's ability to manage complex compliance challenges efficiently.
Cyber Security Systems Analyst
- Concise and Structured Presentation - The CV is well-organized, with sections clearly delineated and content concisely presented. Each job role is detailed with bullet points, making it easy to read and ensuring that key achievements and responsibilities are immediately apparent.
- Strategically Varied Career Trajectory - Ava's career path shows a clear growth trajectory from an IT Governance Consultant to her current role as a Cyber Security Specialist. Her progression reflects a deepening expertise in cybersecurity and risk management, underpinned by experience in top-tier consulting firms.
- Technical Proficiency and Industry Tools - The CV emphasizes Ava's proficiency in a broad range of cybersecurity tools and methodologies, including SIEM, WAF, IAM, PCI-DSS, Cyber Essentials, and familiarity with frameworks like ISO 27001 and NIST. This showcases her technical depth and capability to implement industry-standard security practices.
Cyber Security Forensic Analyst
- Structured and Concise Content Presentation - The CV is well-structured, presenting information clearly and concisely. Sections are logically ordered, which facilitates easy navigation. This clarity allows recruiters to quickly grasp the candidate's qualifications and achievements, making it effective for screening processes.
- Steady Career Growth and Industry Commitment - Theodore Green's career trajectory reflects steady progression from a Forensic Analyst to a Senior Digital Forensic Analyst, highlighting growth and increased responsibility. His commitment to the field is evident through the pursuit of advanced forensic techniques and methodologies, demonstrating long-term dedication to digital forensic analysis and IT security.
- Emphasis on Technical Expertise and Methodologies - The CV showcases unique industry-specific elements, emphasizing proficiency in critical forensic tools such as AXIOM, EnCase, and X-Ways. This technical depth is crucial for a forensic analyst role, where detailed digital investigations and software expertise are paramount. Furthermore, adherence to ISO standards and pioneering new digital evidence preservation protocols reflects high-level competence and technical acumen.
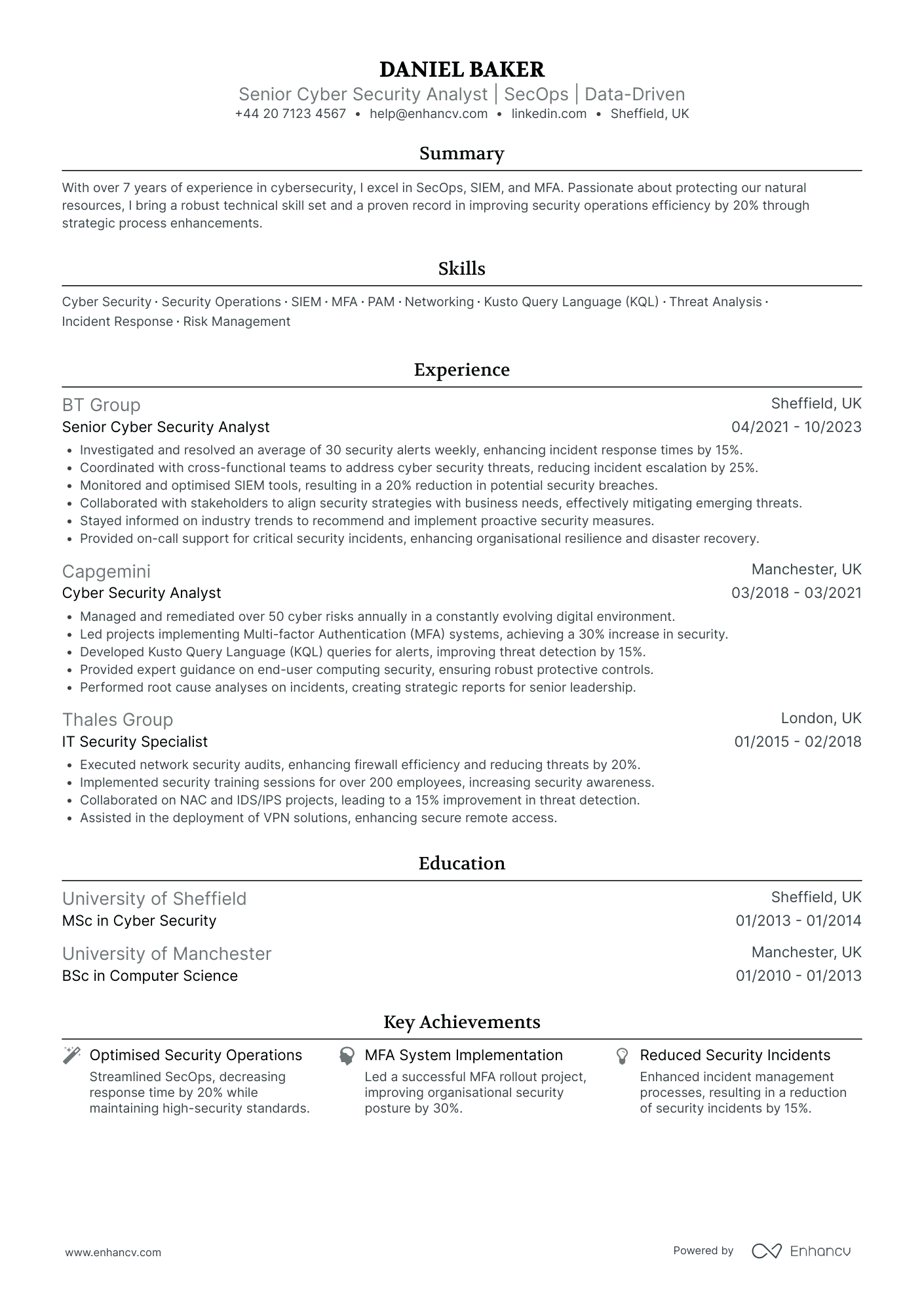
Cyber Security Operations Analyst
- Clear Structure and Conciseness - The CV is well-structured, with sections like experience, education, skills, courses, achievements, and passions clearly delineated, making it easy for the reader to quickly find relevant information. Each section is concise, with bullet points used effectively to communicate key information swiftly.
- Demonstrated Career Growth and Expertise - Alexander's career trajectory is evident, progressing from an Information Security Engineer to a Senior CSOC Analyst. This growth reflects a deepening of expertise and increasing levels of responsibility, aligning with industry demands and showcasing a proactive approach to career advancement.
- Emphasis on Industry-Specific Skills and Tools - The CV highlights Alexander’s proficiency in industry-specific methodologies and technologies such as MITRE ATT&CK, SQL, Python, and cloud security, which are critical in the cybersecurity domain. This demonstrates not only technical competency but also a strong grasp of the tools necessary for effective threat detection and incident response.
Cyber Security Incident Response Analyst
- Clear Structuring and Conciseness - Matilda's CV is well-structured and concise, presenting information in a way that is easy to digest. The use of bullet points in the experience section ensures clarity and allows readers to quickly grasp her accomplishments and responsibilities. The content is direct and focused, which effectively communicates her capabilities without overwhelming the reader with excessive details.
- Impressive Career Growth and Industry Commitment - Matilda's career trajectory showcases significant growth and dedication to the field of cybersecurity. She has progressed from a Security Operations Specialist to a Senior Cybersecurity Analyst, indicating an increase in responsibility and expertise. This upward mobility, coupled with experience at prestigious firms like Deloitte and KPMG, highlights her commitment to her profession and her ability to thrive in the cybersecurity industry.
- Demonstrated Impact with Strategic Achievements - The CV highlights Matilda's ability to make a tangible impact through her achievements. For instance, her implementation of threat detection protocols resulted in a significant 40% reduction in the organizational threat landscape. These accomplishments are not just numbers; they underscore her strategic initiatives' real-world business relevance, proving her value to any potential employer in enhancing cybersecurity defenses.
Cyber Security Vulnerability Analyst
- Structured presentation facilitates readability - The CV is well-organized with clearly defined sections, making it easy for readers to navigate through details. Each portion, from professional experience to education, is concise yet informative, allowing hiring managers to quickly grasp Harry’s capabilities and achievements.
- Continuous career growth in cyber security - Harry Williams’ professional journey reflects substantial growth and adaptation within the cyber security field. Progressing from a Network Security Consultant to a Senior Cyber Security Analyst, the trajectory showcases an increase in responsibility and expertise, highlighting his dedication to mastering complex security challenges.
- Expertise in specialized tools and methodologies - The CV emphasizes Harry’s proficiency in key cyber security tools and techniques such as EDR, SIEM, and IDS, demonstrating his technical depth and alignment with industry trends. His ability to employ these tools for early threat detection and process automation underscores his specialized skill set in vulnerability management and incident response.
Cyber Security Business Analyst
- Impactful Career Growth - Ethan's CV showcases a remarkable career trajectory within the cybersecurity domain, beginning as a Security Analyst at Capgemini and advancing to a Senior Security Consultant at KPMG UK, before attaining a managerial role at BT Group. This progression reflects a deepening expertise and growing leadership responsibilities, painting a clear picture of personal and professional development.
- Comprehensive Skill Set with Technical Precision - The CV highlights a robust set of cybersecurity and risk management skills, complemented by advanced certifications like CISSP. Ethan demonstrates technical proficiency in deploying security policies, conducting risk assessments, and spearheading crisis management, ensuring a blend of tactical and strategic capabilities aligned with industry demands.
- Achievements and Strategic Influence - Ethan’s accomplishments, such as improving incident response time by 30% and reducing security incidents by 25%, are backed by specific statistics, emphasizing his efficacy in enhancing business resilience. His initiatives not only contributed to operational enhancements but also fortified client trust and compliance across organizations.
Cyber Security Network Analyst
- Comprehensive Career Trajectory and Growth - Oliver Smith's career demonstrates a clear progression in the field of cyber security. Starting as a Security Consultant at Siemens, Oliver advanced to an Information Security Analyst at EDF Energy, and eventually to a Cyber Security Analyst at National Grid. This path reflects consistent growth and specialization in the industry, showcasing an ability to adapt and take on more complex responsibilities over time.
- Strong Focus on Impactful Achievements - The CV highlights Oliver's significant contributions through quantifiable results, such as a 30% reduction in security breaches and a 40% mitigation of potential threats. These achievements are not just presented as numbers; they are tied to business impact, demonstrating Oliver's effectiveness in implementing security strategies that have tangible positive outcomes on organizational objectives.
- Clear Presentation of Technical Skills and Qualifications - The CV is well-structured, offering a concise yet comprehensive list of technical skills such as Risk Assessment, Incident Response, and Security Monitoring Systems. Certifications like CompTIA Security+, CISM, and CISSP further bolster Oliver's credentials, establishing a solid foundation of expertise and credibility in cyber security methodologies and tools.
Cyber Security Policy Analyst
- Structured Experience Segmentation - The CV is organized into distinct and clearly labeled sections, offering a concise and structured presentation of the candidate's experience, skills, and achievements. This structure allows the reader to effortlessly navigate through the document and grasp the candidate's qualifications and professional journey quickly.
- Consistent Career Growth and Specialization - Noah Jones's career trajectory illustrates a clear progression from Policy Researcher to Policy Advisor, indicating both growth and depth in the field of public policy. His positions at esteemed institutions like Chatham House and the Overseas Development Institute demonstrate a continuous focus on policy-related roles with increasing responsibilities over time, emphasizing his dedication to this area of expertise.
- Industry-Specific Influence and Innovation - The CV highlights unique elements of Noah’s work in public policy, such as developing strategic frameworks and enhancing stakeholder engagement. The emphasis on impactful projects, like international agreements and climate resilience strategies, showcases his ability to implement innovative methodologies that drive substantive change within his industry.
Cyber Security Application Analyst
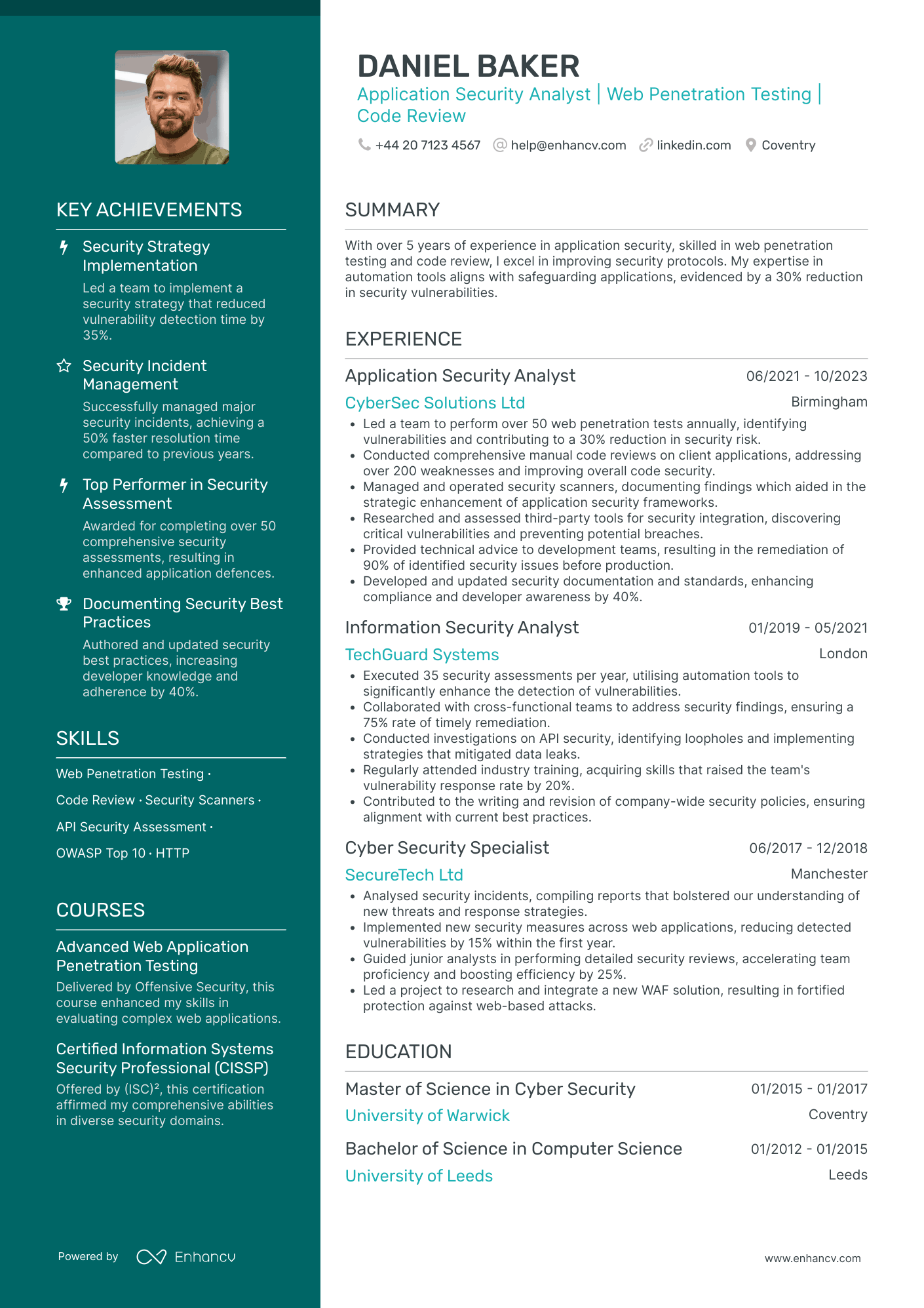
- Clear and Structured Presentation - The CV's organization facilitates easy navigation, with each section clearly labeled and filled with concise information. This clarity helps recruiters understand Daniel Baker's qualifications and accomplishments quickly, emphasizing key aspects such as experience, skills, and education.
- Demonstrated Career Growth and Industry Expertise - Daniel's career trajectory showcases a progression from a Cyber Security Specialist to an Application Security Analyst, highlighting his advancement within the cybersecurity industry. His continuous professional development is evident in his progressively responsible roles and diverse experiences across companies.
- Technical Depth in Security Tools and Methodologies - The CV demonstrates a deep understanding of cybersecurity tools and methodologies, featuring expertise in web penetration testing, code review, and security scanners. Daniel's experience with industry-specific protocols like OWASP Top 10 and various programming languages underlines his technical proficiency.
Cyber Security Data Analyst
- Focused and Structured Content Presentation - The CV excel in its clarity and structured presentation, immediately drawing attention to Sophia's impressive credentials. Key sections are well-organized, highlighting the candidate's professional journey, skills, and achievements with precise bullet points that convey impactful information succinctly.
- Dynamic Career Trajectory - Sophia's career trajectory is a testament to robust growth and advancement. Beginning with technical roles in data engineering, she advanced to senior positions in major banking institutions, reflecting promotions driven by expertise in cybersecurity and data analytics. Her journey from a Data Engineer to Principal Cybersecurity Analytics Data Engineer underscores a thoughtful progression marked by a deepening in responsibility and influence.
- Comprehensive Skill Set with Industry-Specific Expertise - Highlighted throughout the CV is Sophia's deep proficiency in industry-relevant tools and methodologies such as Azure DevOps, Python, and Kubernetes. These skills are not just listed but demonstrated through real-world implementations in projects like cloud migration and data pipeline optimization, indicating both technical depth and vocational relevance.
Cyber Security Audit Analyst
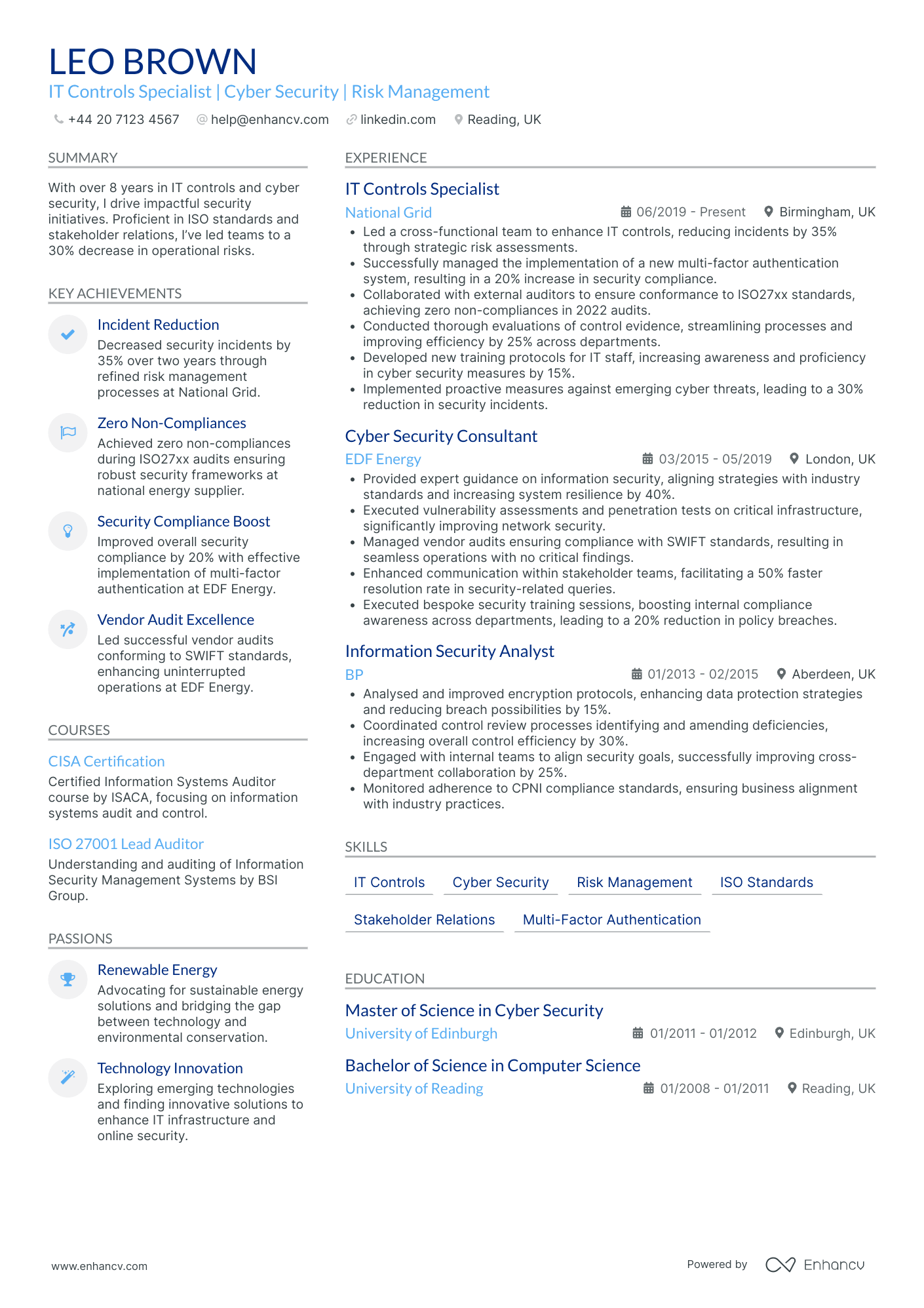
- Emphasizes Leadership and Strategic Initiatives - This CV clearly demonstrates the individual’s leadership capabilities and strategic mindset by detailing accomplishments in decreasing operational risks and improving security compliance. Leading cross-functional teams and managing vendor audits effectively indicates a strong ability to drive significant positive changes within large organizations.
- Solid Evidence of Technical Mastery and Industry Standards - The document highlights the candidate's expertise with industry-specific standards and tools, such as ISO 27001, COBIT, and SWIFT compliance. This depth of technical knowledge, alongside proficiency with multi-factor authentication systems, underscores a robust capability in maintaining and enhancing IT and cyber security systems.
- Showcases a Diverse and Robust Skill Set - Leo Brown’s CV presents a comprehensive skill set encompassing IT controls, risk management, and cyber security. Additionally, it underscores the importance of soft skills, featuring problem-solving and technical communication capabilities essential for stakeholder relations and cross-departmental collaboration, reflecting a versatile professional capable of navigating various business environments.
Formatting your cyber security analyst CV to meet the role expectations
Staring at the blank page for hours on end, you still have no idea how you should start your professional cyber security analyst CV. Should you include more colours, two columns, and which sections? What you should remember about your CV format is this - ensure it's minimalistic and doesn't go over the top with fancy fonts and many colours. Instead, focus on writing consistent content that actually answers the job requirements. But, how about the design itself :
- Use the reverse chronological order to showcase your experience, starting with your most recent role;
- Include your contact details (email address, phone number, and location) - and potentially your professional photo - in the header;
- Must-have CV sections include summary or objective, experience, education, and skills: curate the ones that fit your profile;
- Your professional cyber security analyst CV should be between one-to-two pages long: select the longer format if you have more experience.
A little bit more about your actual CV design, ensure you're using:
- plenty of serif or sans serif font (e.g. Montserrat, Exo 2, Volkhov) as they are Applicant Tracker System (ATS) compliant. Avoid the likes of Arial and Times New Roman because most candidates' CVs are in this typography.
When submitting your CV, are you still not sure what format it should be? Despite the myth that has been circling around, most modern ATS systems are perfectly capable of reading PDFs. This format is an excellent choice as it keeps all of your information intact.

PRO TIP
Incorporate a touch of colour in headers or section breaks, but keep it professional and ensure it doesn’t detract from readability, especially in more conservative industries.
The top sections on a cyber security analyst CV
- Summary of Qualifications highlights your expertise in cyber security and sets the tone.
- Technical Skills showcases specific cyber security tools and technologies you're proficient in.
- Professional Experience details your relevant work history and cyber defence accomplishments.
- Certifications and Training emphasise your commitment to staying current in cyber security trends.
- Projects and Achievements demonstrate practical applications of your skills in real-world scenarios.

What recruiters value on your CV:
- Highlight your technical skills, including proficiency in operating systems, networking, and security tools such as firewalls, antivirus software, and intrusion detection systems, as these are crucial for a cybersecurity analyst role.
- Detail any experience with cyber threat intelligence, including the ability to analyse and interpret data related to cyber threats and vulnerabilities, since identifying risks is a key part of the job.
- Showcase your certifications such as Certified Information Systems Security Professional (CISSP) or Certified Ethical Hacker (CEH), as they are highly valued in the cybersecurity industry and demonstrate a professional commitment to the field.
- Include any relevant experience in creating and maintaining security documentation such as policies, procedures, and incident reports to demonstrate your capability to handle documentation requirements in cybersecurity.
- Emphasise your soft skills, particularly in areas such as problem-solving, attention to detail, and clear communication, which are essential for collaborating with teams and conveying complex security information effectively.
Recommended reads:
Tips and tricks on writing a job-winning cyber security analyst CV header
The CV header is the space which most recruiters would be referring most often to, in the beginning and end of your application. That is as the CV header includes your contact details, but also a headline and a professional photo. When writing your CV header:
- Double-check your contact details for spelling errors or if you've missed any digits. Also, ensure you've provided your personal details, and not your current work email or telephone number;
- Include your location in the form of the city and country you live in. If you want to be more detailed, you can list your full address to show proximity to your potential work place;
- Don't include your CV photo, if you're applying for roles in the UK or US, as this may bias initial recruiters' assessments;
- Write a professional headline that either integrates the job title, some relevant industry keywords, or your most noteworthy achievement.
In the next part of our guide, we'll provide you with professional CVs that showcase some of the best practices when it comes to writing your headline.

Examples of good CV headlines for cyber security analyst:
- Cyber Security Analyst | Threat Detection Specialist | CISSP Certified | 5+ Years Experience
- Senior Cyber Security Expert | Penetration Testing | Compliance & Risk Management | CISM | 8 Years in Field
- Information Security Analyst | Incident Response | Vulnerability Assessment | CEH | 10 Years' Track Record
- Lead Cyber Defence Strategist | Network Security Architect | GDPR Knowledge | CISSP | 12 Years Professional
- Junior Cyber Security Operative | Intrusion Prevention | Cybersecurity Essentials Certified | Enthusiastic Learner | 2 Years Exp.
- Principal Threat Intelligence Analyst | Forensics Expert | Encryption & Cryptography | SANS GIAC | 15+ Years Experience
Choosing your opening statement: a cyber security analyst CV summary or objective
At the top one third of your CV, you have the chance to make a more personable impression on recruiters by selecting between:
- Summary - or those three to five sentences that you use to show your greatest achievements. Use the CV summary if you happen to have plenty of relevant experience and wish to highlight your greatest successes;
- Objective - provides you with up to five sentences to state your professional aims and mission in the company you're applying for

CV summaries for a cyber security analyst job:
- Seasoned Cyber Security Analyst with over 8 years of experience in monitoring, detecting, and neutralizing digital threats. Expert in advanced persistent threats and network defence tactics, with a key achievement in designing a threat detection system that reduced breach incidents by 40% at TechGuard Solutions.
- Diligent Network Administrator with a decade of experience, transitioning into Cyber Security. Proficient in network infrastructure management with a passion for learning and applying the latest security protocols. Notable past achievement includes implementing a network redesign that improved system uptime by 20%.
- Accomplished Software Developer making a career pivot into Cyber Security, bringing a strong foundation in coding and system design. Skilled in Python, Java, and secure coding practices, with a marked success in developing an encryption algorithm adopted by FinTech Corp for safeguarding transaction data.
- Adaptable professional with 5 years in risk analysis, eager to apply analytical skills to Cyber Security challenges. With extensive experience in data analysis and process improvement, I led a project that resulted in a 30% increase in operational efficiency at Dynamic Risk Solutions.
- Eager to embark on a Cyber Security journey, offering strong analytical skills, quick learning abilities, and a keen interest in combating cybercrime. Committed to excellence, I am looking to leverage my problem-solving expertise and enthusiasm for technology to help protect digital assets.
- Aspiring Cyber Security Analyst with a solid foundation in information technology principles, ready to specialize in cyber threat identification and response. My objective is to utilize my strong background in IT support, coupled with a passion for digital security, to contribute to safeguarding an organization's data integrity.
Narrating the details of your cyber security analyst CV experience section
Perhaps you've heard it time and time again, but, how you present your experience is what matters the most. Your CV experience section - that details your work history alongside your accomplishments - is the space to spotlight your unqiue expertise and talents. So, avoid solely listing your responsibilities, but instead:
- adverts' keywords and integrate those in your experience section;
- Use your CV to detail how you've been promoted in the past by including experience in the reverse chronological order.
Before you start writing your cyber security analyst CV experience section, dive into some industry-leading examples on how to structure your bullets.

Best practices for your CV's work experience section
- Analysed and mitigated network vulnerabilities through regular penetration testing and security audits, enhancing overall system security. Developed and documented comprehensive risk assessments and mitigation strategies for various IT projects.
- Managed incident response activities for security breaches and cyber-attacks, minimising impact and recovery time. Crafted post-incident reports with detailed analysis and recommendations for avoiding future incidents.
- Implemented and monitored enterprise security solutions including firewalls, intrusion detection systems, and antivirus software, ensuring robust protection against threats. Tailored security measures to fit organisational needs and resource constraints.
- Conducted regular security awareness training sessions for staff, equipping them with knowledge to identify and prevent potential threats. Developed engaging training materials relevant to the organisation's risk profile.
- Collaborated with IT teams to ensure security measures are integrated into all aspects of network and software development life cycles. Actively participated in design reviews to advocate for security best practices.
- Performed forensic analysis on compromised systems to identify the root cause of security breaches. Created detailed reports and presented findings to senior management to inform about incident specifics and consequences.
- Stayed abreast of the latest cyber security threats and trends, applying this knowledge to enhance the organisation's defensive strategies. Contributed to security policy development and revision, aligning with evolving regulatory requirements and industry standards.
- Monitored security systems for unusual activities using SIEM tools, and fine-tuned system configurations to reduce false positives while effectively identifying genuine threats. Routinely tested response protocols to ensure rapid and efficient action in real scenarios.
- Assisted with compliance audits, ensuring adherence to GDPR, ISO 27001, and other relevant cyber security frameworks. Prepared documentation and evidence to demonstrate compliance and addressed any identified compliance gaps promptly.
- Spearheaded a company-wide vulnerability assessment and penetration testing project, reducing security incidents by 40% within a year.
- Led the integration of a new SIEM solution that allowed for real-time security monitoring and reduced false positive alerts by 25%.
- Conducted training sessions for in-house and remote teams, increasing organisational cybersecurity awareness and reducing phishing success by 35%.
- Developed and maintained threat intelligence platforms, identifying over 100 potential external threats monthly and enhancing threat response time by 20%.
- Collaborated with industry partners to share cyber threat intelligence, contributing to a 30% reduction in threat landscape for sector.
- Authored comprehensive risk analysis reports, which influenced the strategic decisions to invest in specific cybersecurity technologies and protocols.
- Performed risk assessments on over 300 applications and infrastructure components annually, ensuring compliance with industry standards such as ISO 27001.
- Optimized cybersecurity risk management processes, which resulted in a 15% efficiency gain in risk remediation activities.
- Implemented a new risk assessment tool that led to a 50% reduction in time spent on documenting and analysing risks.
- Managed incident response for high-severity incidents, successfully mitigating 95% within the critical one-hour response time.
- Optimised existing threat detection algorithms, reducing the number of undetected malware instances by 60% over six months.
- Developed and implemented a new set of security operation protocols that became the standard across the organisation.
- Conducted regular compliance audits, ensuring the company adhered to regulatory standards and reduced compliance risks by 40%.
- Played a key role in the remediation of audit findings, leading to a pass rate of 98% in subsequent compliance audits.
- Enhanced data protection strategies, leading to significant reductions in personally identifiable information (PII) breaches.
- Oversaw the deployment of advanced network security measures, which decreased network intrusions by 50% in the first six months.
- Developed a security dashboard that provided executives with a clear view of network security status, streamlining decision-making processes.
- Enhanced the encryption protocols across the company's internal communications, significantly improving data integrity and confidentiality.
- Conducted forensic analysis for high-profile data breach incidents, contributing to the identification of threats and securing the digital assets.
- Implemented a new digital evidence management system that improved evidence tracking and reduced case resolution times by 30%.
- Led training modules for junior analysts on forensic tools and techniques, improving departmental skill set and readiness.
- Developed an internal threat intelligence system that tracked and analyzed emerging cybersecurity threats, improving threat response times by 25%.
- Coordinated security efforts with the global security team, ensuring a unified approach to mitigating threats across all company branches.
- Conducted detailed malware analysis, resulting in the discovery of a zero-day exploit and the prompt resolution of the threat before any data compromise.
How to ensure your cyber security analyst CV stands out when you have no experience
This part of our step-by-step guide will help you substitute your experience section by helping you spotlight your skill set. First off, your ability to land your first job will depend on the time you take to assess precisely how you match the job requirements. Whether that's via your relevant education and courses, skill set, or any potential extracurricular activities. Next:
- Systematise your CV so that it spotlights your most relevant experience (whether that's your education or volunteer work) towards the top;
- Focus recruiters' attention to your transferrable skill set and in particular how your personality would be the perfect fit for the role;
- Consider how your current background has helped you build your technological understanding - whether you've created projects in your free time or as part of your uni degree;
- Ensure you've expanded on your teamwork capabilities with any relevant internships, part-time roles, or projects you've participated in the past.
Recommended reads:

PRO TIP
Talk about any positive changes you helped bring about in your previous jobs, like improving a process or helping increase efficiency.
The CV skills' divide: between hard and soft skills
Of course, you may have read the job requirements plenty of times now, but it's key to note that there is a difference between technical and personal skills. Both are equally relevant to your job application. When writing about your skill set, ensure you've copy-pasted the precise skill from the job requirement. This would not only help you ensure you have the correct spelling, but also pass any Applicant Tracker System (ATS) assessments.
- Hard skills show your technological capabilities. Or whether you'll be a good technical fit to the organisation. Ensure you've spotlighted your hard skills in various sections of your CV (e.g. skills section, projects, experience) by including the technology and what you've attained;
- Soft skills pinpoint your personality and people or communication skills, hinting at if you'll easily accomodate into the team or organisation. Quantify your soft skills in your CV achievements, strengths, summary/objective, and experience sections. Always support your soft skills with how they've helped you grow as a professional.
Top skills for your cyber security analyst CV:
Intrusion detection and prevention
Security Information and Event Management (SIEM)
Network security controls
Incident response and handling
Vulnerability assessment
Penetration testing
Cryptographic protocols
Compliance and auditing
Firewall administration
Threat intelligence analysis
Analytical thinking
Problem-solving
Attention to detail
Effective communication
Teamwork and collaboration
Adaptability
Time management
Continuous learning
Ethical judgment
Stress tolerance

PRO TIP
Focus on describing skills in the context of the outcomes they’ve helped you achieve, linking them directly to tangible results or successes in your career.
Your university degree and certificates: an integral part of your cyber security analyst CV
Let's take you back to your uni days and decide what information will be relevant for your cyber security analyst CV. Once more, when discussing your higher education, select only information that is pertinent to the job (e.g. degrees and projects in the same industry, etc.). Ultimately, you should:
- List only your higher education degrees, alongside start and graduation dates, and the university name;
- Include that you obtained a first degree for diplomas that are relevant to the role, and you believe will impress recruiters;
- Showcase relevant coursework, projects, or publications, if you happen to have less experience or will need to fill in gaps in your professional history.

PRO TIP
Order your skills based on the relevance to the role you're applying for, ensuring the most pertinent skills catch the employer's attention first.
Recommended reads:
Key takeaways
Impressing recruiters with your experience, skill set, and values starts with your professional cyber security analyst CV. Write concisely and always aim to answer job requirements with what you've achieved; furthermore:
- Select a simple design that complements your experience and ensures your profile is presentable;
- Include an opening statement that either spotlights your key achievements (summary) or showcases your career ambitions (objective);
- Curate your experience bullets, so that each one commences with a strong, action verb and is followed up by your skill and accomplishment;
- List your hard and soft skills all across different sections of your CV to ensure your application meets the requirements;
- Dedicate space to your relevant higher education diplomas and your certificates to show recruiters you have the necessary industry background.